Privacy Policy | Our customers have two very important questions: Are any of the products they use vulnerable to this zero-day? and Can their security tools help to detect or prevent adversaries from exploiting the vulnerability?. Infoblox NetMRI 7.1.1 has Reflected Cross-Site Scripting via the /api/docs/index.php query parameter. Choose the account you want to sign in with. Are we missing a CPE here?  No, both options are not required. Windows DNS Server is a core networking component. The following registry modification has been identified as a workaround for this vulnerability. https://nvd.nist.gov. WebThis page lists vulnerability statistics for all products of Infoblox. 3 salaries for 3 jobs at Infoblox in Miami-Fort Lauderdale, FL Area. This post is also available in: (Japanese) Executive Summary.
No, both options are not required. Windows DNS Server is a core networking component. The following registry modification has been identified as a workaround for this vulnerability. https://nvd.nist.gov. WebThis page lists vulnerability statistics for all products of Infoblox. 3 salaries for 3 jobs at Infoblox in Miami-Fort Lauderdale, FL Area. This post is also available in: (Japanese) Executive Summary.  This issue results from a flaw in Microsofts DNS server role implementation and affects all Windows Server versions. You can view products of this vendor or security vulnerabilities related to products of A registry-based workaroundcan be used to help protect an affected Windows server, and it can be implemented without requiring an administrator to restart the server. these sites. Investigative efforts are still ongoing for all Log4j-related vulnerabilities, including, We are aware that a vulnerability exists in NetMRI. This advisory describes a Critical Remote Code Execution (RCE) vulnerability that affects Windows servers that are configured to run the DNS Server role. Some examples of configurations that will be vulnerable are: Resolvers using per zone or global forwarding |
You mustrestart the DNS Service for the registry change to take effect. A privilege escalation vulnerability in the "support access" feature on Infoblox NIOS 6.8 through 8.4.1 could allow a locally authenticated administrator to temporarily gain additional privileges on an affected device and perform actions within the super user scope. This playbook will first make a backup of the HKLM registry and will save this backup to the root of the C: drive. This advisory describes a Critical Remote Code Execution (RCE) vulnerability that affects Windows servers that are configured to run the DNS Server role. It is vital that an organizations security infrastructure does not itself introduce any security vulnerabilities.
This issue results from a flaw in Microsofts DNS server role implementation and affects all Windows Server versions. You can view products of this vendor or security vulnerabilities related to products of A registry-based workaroundcan be used to help protect an affected Windows server, and it can be implemented without requiring an administrator to restart the server. these sites. Investigative efforts are still ongoing for all Log4j-related vulnerabilities, including, We are aware that a vulnerability exists in NetMRI. This advisory describes a Critical Remote Code Execution (RCE) vulnerability that affects Windows servers that are configured to run the DNS Server role. Some examples of configurations that will be vulnerable are: Resolvers using per zone or global forwarding |
You mustrestart the DNS Service for the registry change to take effect. A privilege escalation vulnerability in the "support access" feature on Infoblox NIOS 6.8 through 8.4.1 could allow a locally authenticated administrator to temporarily gain additional privileges on an affected device and perform actions within the super user scope. This playbook will first make a backup of the HKLM registry and will save this backup to the root of the C: drive. This advisory describes a Critical Remote Code Execution (RCE) vulnerability that affects Windows servers that are configured to run the DNS Server role. It is vital that an organizations security infrastructure does not itself introduce any security vulnerabilities.  Hone your Ansible skills in lab-intensive, real-world training with any of our Ansible focused courses. Please let us know, "SigRed" - Microsoft Windows Domain Name System (DNS) Server Remote Code Execution Vulnerability. "Support access" is disabled by default. Corporation. When AutoUpdate is enabled, the hotfix has already been pushed to customer devices. |
Accessibility
The registry setting is specific to inbound TCP based DNS response packets and does not globally affect a systems processing of TCP messages in general. Guidance for this workaround can be found at KB4569509: Guidance for DNS Server Vulnerability CVE-2020-1350. Therefore,it is possible that some queries mightnot be answered. by Terms of Use | This Industrial space is available for lease. Once we had this view, our internal Red Team was able to create a test to validate if an instance of Log4j in our environment could be exploited.
Hone your Ansible skills in lab-intensive, real-world training with any of our Ansible focused courses. Please let us know, "SigRed" - Microsoft Windows Domain Name System (DNS) Server Remote Code Execution Vulnerability. "Support access" is disabled by default. Corporation. When AutoUpdate is enabled, the hotfix has already been pushed to customer devices. |
Accessibility
The registry setting is specific to inbound TCP based DNS response packets and does not globally affect a systems processing of TCP messages in general. Guidance for this workaround can be found at KB4569509: Guidance for DNS Server Vulnerability CVE-2020-1350. Therefore,it is possible that some queries mightnot be answered. by Terms of Use | This Industrial space is available for lease. Once we had this view, our internal Red Team was able to create a test to validate if an instance of Log4j in our environment could be exploited.  Cisco has addressed this vulnerability. the facts presented on these sites. AKA SIGRed (CVE-2020-1350) is a wormable, critical vulnerability (CVSS base score of 10.0) in the Windows DNS server that affects Windows Server versions 2003 to 2019.
Cisco has addressed this vulnerability. the facts presented on these sites. AKA SIGRed (CVE-2020-1350) is a wormable, critical vulnerability (CVSS base score of 10.0) in the Windows DNS server that affects Windows Server versions 2003 to 2019.  After the update has been applied, the workaround is no longer needed and should be removed. However, it can be pasted. A successful mitigation will show the following: Remediating vulnerabilities in network devices and servers is crucial, and in this blog we showed how Ansible can help with that given the current example of the CVE-2020-1350 | Windows DNS Server Remote Code Execution Vulnerability. Value =TcpReceivePacketSize
No. A .gov website belongs to an official government organization in the United States.
After the update has been applied, the workaround is no longer needed and should be removed. However, it can be pasted. A successful mitigation will show the following: Remediating vulnerabilities in network devices and servers is crucial, and in this blog we showed how Ansible can help with that given the current example of the CVE-2020-1350 | Windows DNS Server Remote Code Execution Vulnerability. Value =TcpReceivePacketSize
No. A .gov website belongs to an official government organization in the United States.  Updates to this vulnerability are available. If you are unable to apply the update right away, you will be able to protect your environment before your standard cadence for installing updates. We employ security systems that can detect and prevent attempted exploits of this vulnerability in our environment. Anyterm Daemon in Infoblox Network Automation NetMRI before NETMRI-23483 allows remote attackers to execute arbitrary commands with root privileges via a crafted terminal/anyterm-module request. A remote code execution vulnerability exists in Windows Domain Name System servers when they fail to properly handle requests, aka 'Windows DNS Server Remote Code Execution Vulnerability'.
Updates to this vulnerability are available. If you are unable to apply the update right away, you will be able to protect your environment before your standard cadence for installing updates. We employ security systems that can detect and prevent attempted exploits of this vulnerability in our environment. Anyterm Daemon in Infoblox Network Automation NetMRI before NETMRI-23483 allows remote attackers to execute arbitrary commands with root privileges via a crafted terminal/anyterm-module request. A remote code execution vulnerability exists in Windows Domain Name System servers when they fail to properly handle requests, aka 'Windows DNS Server Remote Code Execution Vulnerability'. 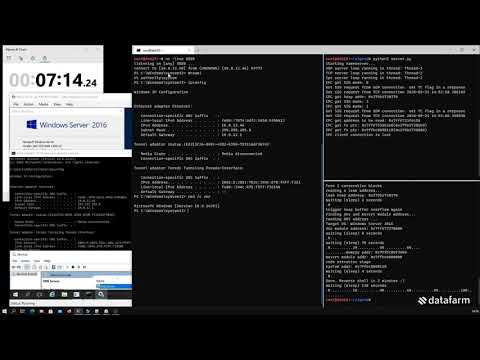 may have information that would be of interest to you. To eliminate any possibility of exploiting the above vulnerabilities, Infoblox strongly recommends applying the attached Hotfix that is specific to the NIOS version you are running. It is possible for BIND to be abused in a reflection attack with a very high amplification factor. To work around thisvulnerability, make the following registry changeto restrictthe size of the largest inbound TCP-based DNS response packet that's allowed: Key:HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\DNS\Parameters
|
Secure .gov websites use HTTPS
If you are unable to apply the update right away, you will be able to protect your environment before your standard cadence for installing updates. |
On May 19, 2020, ISC announcedCVE-2020-8617. (See KB Article 000007559). If so, please click the link here. For more details, please refer to our, Infoblox Response to Apache Log4j Vulnerability, On December 10th, a zero-day vulnerability (, ) was discovered in a popular Java-based logging audit framework within Apache called Log4j. these sites. This type of exploit is known as an NXNSAttack. Science.gov
To do this,run the following command at an elevated command prompt: After the workaround is implemented, a Windows DNS server will be unable to resolve DNS names for its clients if the DNS response from the upstream server is larger than 65,280 bytes. Corporation. While this vulnerability is not currently known to be used in active attacks, it is essential that customers apply Windows updates to address this vulnerability as soon as possible. Commerce.gov
This vulnerability exists within the Microsoft Windows Domain Name System (DNS) Server WebWe would like to show you a description here but the site wont allow us. A successful exploit could allow the attacker to negatively A registry-based workaroundcan be used to help protect an affected Windows server, and it can be implemented without requiring an administrator to restart the server. | Windows DNS Server Remote Code Execution Vulnerability. A vulnerability in the web UI of Cisco Umbrella could allow an unauthenticated, remote attacker to negatively affect the performance of this service. However, doing so manually is time consuming and prone to error, especially if many servers are involved.
may have information that would be of interest to you. To eliminate any possibility of exploiting the above vulnerabilities, Infoblox strongly recommends applying the attached Hotfix that is specific to the NIOS version you are running. It is possible for BIND to be abused in a reflection attack with a very high amplification factor. To work around thisvulnerability, make the following registry changeto restrictthe size of the largest inbound TCP-based DNS response packet that's allowed: Key:HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\DNS\Parameters
|
Secure .gov websites use HTTPS
If you are unable to apply the update right away, you will be able to protect your environment before your standard cadence for installing updates. |
On May 19, 2020, ISC announcedCVE-2020-8617. (See KB Article 000007559). If so, please click the link here. For more details, please refer to our, Infoblox Response to Apache Log4j Vulnerability, On December 10th, a zero-day vulnerability (, ) was discovered in a popular Java-based logging audit framework within Apache called Log4j. these sites. This type of exploit is known as an NXNSAttack. Science.gov
To do this,run the following command at an elevated command prompt: After the workaround is implemented, a Windows DNS server will be unable to resolve DNS names for its clients if the DNS response from the upstream server is larger than 65,280 bytes. Corporation. While this vulnerability is not currently known to be used in active attacks, it is essential that customers apply Windows updates to address this vulnerability as soon as possible. Commerce.gov
This vulnerability exists within the Microsoft Windows Domain Name System (DNS) Server WebWe would like to show you a description here but the site wont allow us. A successful exploit could allow the attacker to negatively A registry-based workaroundcan be used to help protect an affected Windows server, and it can be implemented without requiring an administrator to restart the server. | Windows DNS Server Remote Code Execution Vulnerability. A vulnerability in the web UI of Cisco Umbrella could allow an unauthenticated, remote attacker to negatively affect the performance of this service. However, doing so manually is time consuming and prone to error, especially if many servers are involved. 
 Several other nameservers are also known to behave similarly and the reporters are coordinating a response among multiple vendors. For a more detailed analysis of the vulnerability exploitation, please read this Cyber Campaign Brief or watch the video below. Further, NIST does not
This will check the that the TcpReceivePacketSize value exists and is set to 0xff00. As Infoblox learns more about the threats involved, we will continue to update our Threat Intelligence feeds. CVE is sponsored by the U.S. Department of Homeland Security (DHS) Cybersecurity and Infrastructure Security Agency (CISA). No
We have already communicated directly with impacted organizations and are working to help them remediate this threat as quickly as possible and limit their exposure. This post describes the exploitation (RCE) of SIGRed (CVE-20201350) on Windows Server 2012 R2 to Windows Server 2019. In releases of BIND dating from March 2018 and after, an assertion check in tsig.c detects this inconsistent state and deliberately exits. CVSS Severity Rating Fix Information Vulnerable Software Versions SCAP Mappings CPE Information, You can also search by reference using the, Learn more at National Vulnerability Database (NVD), MISC:http://packetstormsecurity.com/files/158484/SIGRed-Windows-DNS-Denial-Of-Service.html, MISC:https://portal.msrc.microsoft.com/en-US/security-guidance/advisory/CVE-2020-1350, URL:https://portal.msrc.microsoft.com/en-US/security-guidance/advisory/CVE-2020-1350, Cybersecurity and Infrastructure Security Agency, The MITRE Infoblox has been diligently investigating this new threat, and we have concluded that our SaaS products are not subject to this vulnerability at this time. Tickets availablenow. Please address comments about this page to nvd@nist.gov. not necessarily endorse the views expressed, or concur with
Several other nameservers are also known to behave similarly and the reporters are coordinating a response among multiple vendors. For a more detailed analysis of the vulnerability exploitation, please read this Cyber Campaign Brief or watch the video below. Further, NIST does not
This will check the that the TcpReceivePacketSize value exists and is set to 0xff00. As Infoblox learns more about the threats involved, we will continue to update our Threat Intelligence feeds. CVE is sponsored by the U.S. Department of Homeland Security (DHS) Cybersecurity and Infrastructure Security Agency (CISA). No
We have already communicated directly with impacted organizations and are working to help them remediate this threat as quickly as possible and limit their exposure. This post describes the exploitation (RCE) of SIGRed (CVE-20201350) on Windows Server 2012 R2 to Windows Server 2019. In releases of BIND dating from March 2018 and after, an assertion check in tsig.c detects this inconsistent state and deliberately exits. CVSS Severity Rating Fix Information Vulnerable Software Versions SCAP Mappings CPE Information, You can also search by reference using the, Learn more at National Vulnerability Database (NVD), MISC:http://packetstormsecurity.com/files/158484/SIGRed-Windows-DNS-Denial-Of-Service.html, MISC:https://portal.msrc.microsoft.com/en-US/security-guidance/advisory/CVE-2020-1350, URL:https://portal.msrc.microsoft.com/en-US/security-guidance/advisory/CVE-2020-1350, Cybersecurity and Infrastructure Security Agency, The MITRE Infoblox has been diligently investigating this new threat, and we have concluded that our SaaS products are not subject to this vulnerability at this time. Tickets availablenow. Please address comments about this page to nvd@nist.gov. not necessarily endorse the views expressed, or concur with
 Site Privacy
INDIRECT or any other kind of loss. Are you interested in our Early Access Program (EAP)? : CVE-2009-1234 or 2010-1234 or 20101234), Take a third party risk management course for FREE, How does it work? FOIA
|
|
Use of the CVE List and the associated references from this website are subject to the terms of use. For more information, see DNS Logging and Diagnostics. sites that are more appropriate for your purpose. Commerce.gov
This is a potential security issue, you are being redirected to
When AutoUpdate is enabled, the hotfix has already been pushed to customer devices. Customers are advised to write their own playbooks to mitigate the issue. TCP-based DNS response packets that exceed the recommended value will be dropped without error. No actions needed on the NIOS side but remediation is listed above for Windows DNS server. Accessibility
This hotfix has been tested by our internal Red Team and confirmed that NetMRI with the hotfix applied is not vulnerable to the Log4j vulnerabilities. Environmental Policy
About the vulnerability Investigative efforts are still ongoing for all Log4j-related vulnerabilities, including CVE-2017-5645, CVE-2019-17571, CVE-2020-9488, CVE-2021-4104,CVE-2021-45046, CVE-2021-45105, and CVE-2021-44832. An attacker could exploit this vulnerability by sending crafted HTTPS packets at a high and sustained rate. Automating Mitigation of the Microsoft (CVE-2020-1350) Security Vulnerability in Windows Domain Name System Using Ansible Tower, KB4569509: Guidance for DNS Server Vulnerability CVE-2020-1350, Windows Remote Management in the Ansible documentation, *Red Hat provides no expressed support claims to the correctness of this code. inferences should be drawn on account of other sites being
The second task Changing registry settings for DNS parameters makes a change to the registry to restrict the size of the largest inbound TCP-based DNS response packet that's allowed. ALL WARRANTIES OF ANY KIND ARE EXPRESSLY DISCLAIMED. The vulnerability is described in CVE-2020-1350. While this vulnerability is not currently known to be used in active attacks, it is essential that customers apply Windows updates to address this vulnerability as soon as possible. We strongly recommend that server administrators apply thesecurity update at their earliest convenience. There may be other web
Successful exploitation allows attackers to run any code they want with local SYSTEM access. This workaround applies FF00 as the value which has a decimal value of 65280. This site will NOT BE LIABLE FOR ANY DIRECT, Please let us know. The playbook is provided as-is and is only provided for guidance. Ansible is powerful IT automation that you can learn quickly.
CVE-2020-1350 | Windows DNS Server Remote Code Execution Vulnerability. Infoblox NIOS and BloxOne DDI products are not vulnerable CVE-2020-1350 Vulnerability in Windows Domain Name System (DNS) Server. Privacy Policy | However, a non-standard use-case may exist in a given environment. You may withdraw your consent at any time. Yesterday, Microsoft released updates for all supported versions of Windows and Windows Server to address a remote code execution vulnerability in DNS Server, marked as critical. Contact Us |
Site Privacy
INDIRECT or any other kind of loss. Are you interested in our Early Access Program (EAP)? : CVE-2009-1234 or 2010-1234 or 20101234), Take a third party risk management course for FREE, How does it work? FOIA
|
|
Use of the CVE List and the associated references from this website are subject to the terms of use. For more information, see DNS Logging and Diagnostics. sites that are more appropriate for your purpose. Commerce.gov
This is a potential security issue, you are being redirected to
When AutoUpdate is enabled, the hotfix has already been pushed to customer devices. Customers are advised to write their own playbooks to mitigate the issue. TCP-based DNS response packets that exceed the recommended value will be dropped without error. No actions needed on the NIOS side but remediation is listed above for Windows DNS server. Accessibility
This hotfix has been tested by our internal Red Team and confirmed that NetMRI with the hotfix applied is not vulnerable to the Log4j vulnerabilities. Environmental Policy
About the vulnerability Investigative efforts are still ongoing for all Log4j-related vulnerabilities, including CVE-2017-5645, CVE-2019-17571, CVE-2020-9488, CVE-2021-4104,CVE-2021-45046, CVE-2021-45105, and CVE-2021-44832. An attacker could exploit this vulnerability by sending crafted HTTPS packets at a high and sustained rate. Automating Mitigation of the Microsoft (CVE-2020-1350) Security Vulnerability in Windows Domain Name System Using Ansible Tower, KB4569509: Guidance for DNS Server Vulnerability CVE-2020-1350, Windows Remote Management in the Ansible documentation, *Red Hat provides no expressed support claims to the correctness of this code. inferences should be drawn on account of other sites being
The second task Changing registry settings for DNS parameters makes a change to the registry to restrict the size of the largest inbound TCP-based DNS response packet that's allowed. ALL WARRANTIES OF ANY KIND ARE EXPRESSLY DISCLAIMED. The vulnerability is described in CVE-2020-1350. While this vulnerability is not currently known to be used in active attacks, it is essential that customers apply Windows updates to address this vulnerability as soon as possible. We strongly recommend that server administrators apply thesecurity update at their earliest convenience. There may be other web
Successful exploitation allows attackers to run any code they want with local SYSTEM access. This workaround applies FF00 as the value which has a decimal value of 65280. This site will NOT BE LIABLE FOR ANY DIRECT, Please let us know. The playbook is provided as-is and is only provided for guidance. Ansible is powerful IT automation that you can learn quickly.
CVE-2020-1350 | Windows DNS Server Remote Code Execution Vulnerability. Infoblox NIOS and BloxOne DDI products are not vulnerable CVE-2020-1350 Vulnerability in Windows Domain Name System (DNS) Server. Privacy Policy | However, a non-standard use-case may exist in a given environment. You may withdraw your consent at any time. Yesterday, Microsoft released updates for all supported versions of Windows and Windows Server to address a remote code execution vulnerability in DNS Server, marked as critical. Contact Us |  The referenced playbook contains three tasks which each provide the following: Also of note is that this playbook is idempotent in that you can run it multiple times and it results in the same outcome. Infoblox has been diligently investigating this new threat, and we have concluded that our SaaS products are not subject to this vulnerability at this time. Infoblox NetMRI before 6.8.5 has a default password of admin for the "root" MySQL database account, which makes it easier for local users to obtain access via unspecified vectors. Corporation. Product Manager for Threat Intelligence and Analytics here at Infoblox. Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type. WebDescription. Does the workaround apply to all versions of Windows Server? It is suggested that this location be changed to an offbox share. This value is 255 less than the maximum allowed value of 65,535. Will this workaround affect any other TCP based network communications? CVE-2020-8617CVSS Score: 7.4CVSS Vector: CVSS:3.1AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:N/A:HSeverity: HighExploitable: RemotelyWorkarounds: NoneDescription:An error in BIND code which checks the validity of messages containing TSIG resource records can be exploited by an attacker to trigger an assertion failure in tsig.c, resulting in denial of service to clients.Impact:Using a specially-crafted message, an attacker may potentially cause a BIND server to reach an inconsistent state if the attacker knows (or successfully guesses) the name of a TSIG key used by the server. Automating Mitigation of the Microsoft (CVE-2020-1350) Security Vulnerability in Windows Domain Name System Using Ansible Tower August 13, 2020 by
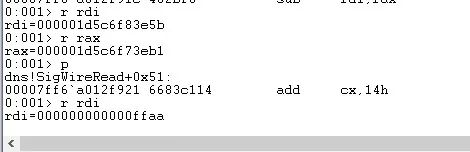
The referenced playbook contains three tasks which each provide the following: Also of note is that this playbook is idempotent in that you can run it multiple times and it results in the same outcome. Infoblox has been diligently investigating this new threat, and we have concluded that our SaaS products are not subject to this vulnerability at this time. Infoblox NetMRI before 6.8.5 has a default password of admin for the "root" MySQL database account, which makes it easier for local users to obtain access via unspecified vectors. Corporation. Product Manager for Threat Intelligence and Analytics here at Infoblox. Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type. WebDescription. Does the workaround apply to all versions of Windows Server? It is suggested that this location be changed to an offbox share. This value is 255 less than the maximum allowed value of 65,535. Will this workaround affect any other TCP based network communications? CVE-2020-8617CVSS Score: 7.4CVSS Vector: CVSS:3.1AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:N/A:HSeverity: HighExploitable: RemotelyWorkarounds: NoneDescription:An error in BIND code which checks the validity of messages containing TSIG resource records can be exploited by an attacker to trigger an assertion failure in tsig.c, resulting in denial of service to clients.Impact:Using a specially-crafted message, an attacker may potentially cause a BIND server to reach an inconsistent state if the attacker knows (or successfully guesses) the name of a TSIG key used by the server. Automating Mitigation of the Microsoft (CVE-2020-1350) Security Vulnerability in Windows Domain Name System Using Ansible Tower August 13, 2020 by  Wormable vulnerabilities have the potential to spread via malware between vulnerable computers without user interaction. On July 14, 2020, Microsoft released a security update for the issue that is described in CVE-2020-1350 | Windows DNS Server Remote Code Execution Vulnerability. This hotfix has been tested by our internal Red Team and confirmed that NetMRI with the hotfix applied is not vulnerable to the Log4j vulnerabilities. Thus lets check that we have been successful: This can also be validated with the following Ansible Playbook. WebInfoblox NIOS is the worlds leading on-premises platform for automating DNS, DHCP and IPAM (DDI)and simplifying complex, dynamic network services for any size As an example, a playbook is included below which, when executed from within Ansible Tower, has been shown to successfully mitigate this security vulnerability. CVE-2020-1350 | Windows DNS Server Remote Code Execution Vulnerability. Infoblox continues to scan our internal network for applications and systems.
Wormable vulnerabilities have the potential to spread via malware between vulnerable computers without user interaction. On July 14, 2020, Microsoft released a security update for the issue that is described in CVE-2020-1350 | Windows DNS Server Remote Code Execution Vulnerability. This hotfix has been tested by our internal Red Team and confirmed that NetMRI with the hotfix applied is not vulnerable to the Log4j vulnerabilities. Thus lets check that we have been successful: This can also be validated with the following Ansible Playbook. WebInfoblox NIOS is the worlds leading on-premises platform for automating DNS, DHCP and IPAM (DDI)and simplifying complex, dynamic network services for any size As an example, a playbook is included below which, when executed from within Ansible Tower, has been shown to successfully mitigate this security vulnerability. CVE-2020-1350 | Windows DNS Server Remote Code Execution Vulnerability. Infoblox continues to scan our internal network for applications and systems.  The provided playbook was written specifically for Ansible Tower and serves as an example of how the mitigation can be carried out. To do this,run the following command at an elevated command prompt: After the workaround is implemented, a Windows DNS server will be unable to resolve DNS names for its clients if the DNS response from the upstream server is larger than 65,280 bytes. inferences should be drawn on account of other sites being
The reduced value is unlikely to affect standard deployments or recursive queries. A remote code execution vulnerability exists in Windows Domain Name System servers when they fail to properly handle requests, aka 'Windows DNS Server Remote Code Execution Vulnerability'. Ansible can help in automating a temporary workaround across multiple Windows DNS servers. This issue has been classified as CWE-835: Loop with Unreachable Exit Condition ('Infinite Loop'). We have provided these links to other web sites because they
Note: A restart of the DNS Service is required to take effect. This advisory describes a Critical Remote Code Execution (RCE) vulnerability that affects Windows servers that are configured to run the DNS Server role. When enabled, the access will be automatically disabled (and support access code will expire) after the 24 hours. the facts presented on these sites. However, the registry modification will no longer be needed after the update is applied.
The provided playbook was written specifically for Ansible Tower and serves as an example of how the mitigation can be carried out. To do this,run the following command at an elevated command prompt: After the workaround is implemented, a Windows DNS server will be unable to resolve DNS names for its clients if the DNS response from the upstream server is larger than 65,280 bytes. inferences should be drawn on account of other sites being
The reduced value is unlikely to affect standard deployments or recursive queries. A remote code execution vulnerability exists in Windows Domain Name System servers when they fail to properly handle requests, aka 'Windows DNS Server Remote Code Execution Vulnerability'. Ansible can help in automating a temporary workaround across multiple Windows DNS servers. This issue has been classified as CWE-835: Loop with Unreachable Exit Condition ('Infinite Loop'). We have provided these links to other web sites because they
Note: A restart of the DNS Service is required to take effect. This advisory describes a Critical Remote Code Execution (RCE) vulnerability that affects Windows servers that are configured to run the DNS Server role. When enabled, the access will be automatically disabled (and support access code will expire) after the 24 hours. the facts presented on these sites. However, the registry modification will no longer be needed after the update is applied. 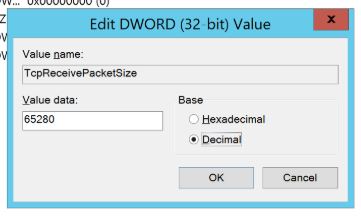 No
Because of the volatility of this vulnerability, administrators may have to implement the workaround before they applythesecurity update in order to enable them to update their systems by using a standard deployment cadence. No, both options are not required. |
No
Because of the volatility of this vulnerability, administrators may have to implement the workaround before they applythesecurity update in order to enable them to update their systems by using a standard deployment cadence. No, both options are not required. |
 Infoblox has been diligently investigating this new threat, and we have concluded that our SaaS products are not subject to this vulnerability at this time. A lock () or https:// means you've safely connected to the .gov website. The following factors need to be considered: In order to successfully run the referenced playbook, you'll need to run this against a Windows server that has the DNS server running. The workaround is compatible with the security update. Type =DWORD
Infoblox has been diligently investigating this new threat, and we have concluded that our SaaS products are not subject to this vulnerability at this time. A lock () or https:// means you've safely connected to the .gov website. The following factors need to be considered: In order to successfully run the referenced playbook, you'll need to run this against a Windows server that has the DNS server running. The workaround is compatible with the security update. Type =DWORD
 Severity CVSS Version 3.x CVSS Version 2.0 CVSS 3.x Severity and Metrics: NIST: NVD An improper handling of exceptional conditions vulnerability in Cortex XDR Agent allows a local authenticated Windows user to create files in the software's internal program directory that prevents the Cortex XDR Agent from starting. Please let us know. Then, you will have to review the log files to identify the presence of anomalously large TCP response packets
RCEs are bad vulnerabilities, unauthenticated ones are even worse. Explore subscription benefits, browse training courses, learn how to secure your device, and more. TCP-based DNS response packets that exceed the recommended value will be dropped without error. During Infobloxs due diligence involving this vulnerability, it has uncovered evidence of invalid DNS queries that we believe may be associated with adversary groups attempting to exploit systems. Re: Cisco AP DHCP Option 43 with Infoblox, How to Accessing the Reporting Server via Splunk API, Infoblox License Expires Information Discrepancy.
Severity CVSS Version 3.x CVSS Version 2.0 CVSS 3.x Severity and Metrics: NIST: NVD An improper handling of exceptional conditions vulnerability in Cortex XDR Agent allows a local authenticated Windows user to create files in the software's internal program directory that prevents the Cortex XDR Agent from starting. Please let us know. Then, you will have to review the log files to identify the presence of anomalously large TCP response packets
RCEs are bad vulnerabilities, unauthenticated ones are even worse. Explore subscription benefits, browse training courses, learn how to secure your device, and more. TCP-based DNS response packets that exceed the recommended value will be dropped without error. During Infobloxs due diligence involving this vulnerability, it has uncovered evidence of invalid DNS queries that we believe may be associated with adversary groups attempting to exploit systems. Re: Cisco AP DHCP Option 43 with Infoblox, How to Accessing the Reporting Server via Splunk API, Infoblox License Expires Information Discrepancy.  |
Reference
Are you interested in our Early Access Program (EAP)? The update and the workaround are both detailed in CVE-2020-1350. It can be triggered by a malicious DNS response. Non-Microsoft DNS Servers are not affected. Share sensitive information only on official, secure websites.
|
Reference
Are you interested in our Early Access Program (EAP)? The update and the workaround are both detailed in CVE-2020-1350. It can be triggered by a malicious DNS response. Non-Microsoft DNS Servers are not affected. Share sensitive information only on official, secure websites.  Privacy Program
A locally authenticated administrative user may be able to exploit this vulnerability if the "support access" feature is enabled, they know the support access code for the current session, and they know the algorithm to generate the support access password from the support access code. Copyright 19992023, The MITRE Copyrights
WebCloud and Virtualization Infoblox DDI for Azure Automate DNS provisioning and virtual networks and virtual machine visibility in your Azure environment Eval ideal for: Organizations seeking DNS automation and visibility for their Azure and/or hybrid cloud deployments Try it now Infoblox DDI for AWS WebCVE-2020-1435 Detail Description A remote code execution vulnerability exists in the way that the Windows Graphics Device Interface (GDI) handles objects in the memory, aka 'GDI+ Remote Code Execution Vulnerability'. The workaround is available on all versions of Windows Server running the DNS role. WebIntroduction On July 14, 2020, Microsoft released a security update for the issue that is described in CVE-2020-1350 | Windows DNS Server Remote Code Execution Follow CVE.
Privacy Program
A locally authenticated administrative user may be able to exploit this vulnerability if the "support access" feature is enabled, they know the support access code for the current session, and they know the algorithm to generate the support access password from the support access code. Copyright 19992023, The MITRE Copyrights
WebCloud and Virtualization Infoblox DDI for Azure Automate DNS provisioning and virtual networks and virtual machine visibility in your Azure environment Eval ideal for: Organizations seeking DNS automation and visibility for their Azure and/or hybrid cloud deployments Try it now Infoblox DDI for AWS WebCVE-2020-1435 Detail Description A remote code execution vulnerability exists in the way that the Windows Graphics Device Interface (GDI) handles objects in the memory, aka 'GDI+ Remote Code Execution Vulnerability'. The workaround is available on all versions of Windows Server running the DNS role. WebIntroduction On July 14, 2020, Microsoft released a security update for the issue that is described in CVE-2020-1350 | Windows DNS Server Remote Code Execution Follow CVE.  In July 2020, Microsoft released a security update, CVE-2020-1350 | Windows DNS Server Remote Code Execution Vulnerability, for a new remote code execution (RCE) vulnerability. referenced, or not, from this page. Due to the serious nature of the threat, Infoblox will add all suspicious indicators to our MalwareC2_Generic threat feeds. CRLF injection vulnerability in Infoblox Network Automation NetMRI before 7.1.1 allows remote attackers to inject arbitrary HTTP headers and conduct HTTP response splitting attacks via the contentType parameter in a login action to config/userAdmin/login.tdf. Home / Security / Infoblox Response to Apache Log4j Vulnerability. Communities help you ask and answer questions, give feedback, and hear from experts with rich knowledge. Follow the steps in this section carefully. #12006: Infoblox NIOS product is vulnerable to CVE #12006: Infoblox NIOS product is vulnerable to CVE-2020-8616 and CVE-2020-8617, Published 05/19/2020 | Updated 06/17/2020 02:30 PM, The performance of the recursing server can potentially be degraded by the additional work required to perform these fetches, and, The attacker can exploit this behavior to use the recursing server as a reflector in a reflection attack with a high amplification factor, If FIPS NIOS software is being run on your grid and this Hotfix is needed, please open up a new Support ticket for this request and a Support Engineer will be able to assist, If your Grid has previously been patched with a Hotfix from Infoblox for a prior issue, please open a Support case (with the following information below)to verify if your prior Hotfix(es) will remain intact after applying this new Hotfix. The vulnerability exists due to insufficient rate limiting controls in the web UI. The vulnerability is due to a weakness in the "support access" password generation algorithm. However, the registry modification will no longer be needed after the update is applied. not necessarily endorse the views expressed, or concur with
Further, NIST does not
sites that are more appropriate for your purpose. Windows servers that are configured as DNS servers are at risk from this vulnerability. This month's release has one critical vulnerability in Microsoft Windows Server (CVE-2020-1350) that allows for remote code execution by an unauthenticated attacker. |
may have information that would be of interest to you. Copyrights
Secure .gov websites use HTTPS
USA.gov, An official website of the United States government, CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:C/C:H/I:H/A:H, http://packetstormsecurity.com/files/158484/SIGRed-Windows-DNS-Denial-Of-Service.html, https://portal.msrc.microsoft.com/en-US/security-guidance/advisory/CVE-2020-1350, Are we missing a CPE here? However, in some use cases, applying the update quickly might not be practical: in many enterprises, even hotfixes need to run through a series of tests that require time. A successful exploit could allow the attacker to negatively affect the performance of the web UI. Because of the volatility of this vulnerability, administrators may have to implement the workaround before they applythesecurity update in order to enable them to update their systems by using a standard deployment cadence. There may be other web
WebIntroduction On July 14, 2020, Microsoft released a security update for the issue that is described in CVE-2020-1350 | Windows DNS Server Remote Code Execution Vulnerability.
In July 2020, Microsoft released a security update, CVE-2020-1350 | Windows DNS Server Remote Code Execution Vulnerability, for a new remote code execution (RCE) vulnerability. referenced, or not, from this page. Due to the serious nature of the threat, Infoblox will add all suspicious indicators to our MalwareC2_Generic threat feeds. CRLF injection vulnerability in Infoblox Network Automation NetMRI before 7.1.1 allows remote attackers to inject arbitrary HTTP headers and conduct HTTP response splitting attacks via the contentType parameter in a login action to config/userAdmin/login.tdf. Home / Security / Infoblox Response to Apache Log4j Vulnerability. Communities help you ask and answer questions, give feedback, and hear from experts with rich knowledge. Follow the steps in this section carefully. #12006: Infoblox NIOS product is vulnerable to CVE #12006: Infoblox NIOS product is vulnerable to CVE-2020-8616 and CVE-2020-8617, Published 05/19/2020 | Updated 06/17/2020 02:30 PM, The performance of the recursing server can potentially be degraded by the additional work required to perform these fetches, and, The attacker can exploit this behavior to use the recursing server as a reflector in a reflection attack with a high amplification factor, If FIPS NIOS software is being run on your grid and this Hotfix is needed, please open up a new Support ticket for this request and a Support Engineer will be able to assist, If your Grid has previously been patched with a Hotfix from Infoblox for a prior issue, please open a Support case (with the following information below)to verify if your prior Hotfix(es) will remain intact after applying this new Hotfix. The vulnerability exists due to insufficient rate limiting controls in the web UI. The vulnerability is due to a weakness in the "support access" password generation algorithm. However, the registry modification will no longer be needed after the update is applied. not necessarily endorse the views expressed, or concur with
Further, NIST does not
sites that are more appropriate for your purpose. Windows servers that are configured as DNS servers are at risk from this vulnerability. This month's release has one critical vulnerability in Microsoft Windows Server (CVE-2020-1350) that allows for remote code execution by an unauthenticated attacker. |
may have information that would be of interest to you. Copyrights
Secure .gov websites use HTTPS
USA.gov, An official website of the United States government, CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:C/C:H/I:H/A:H, http://packetstormsecurity.com/files/158484/SIGRed-Windows-DNS-Denial-Of-Service.html, https://portal.msrc.microsoft.com/en-US/security-guidance/advisory/CVE-2020-1350, Are we missing a CPE here? However, in some use cases, applying the update quickly might not be practical: in many enterprises, even hotfixes need to run through a series of tests that require time. A successful exploit could allow the attacker to negatively affect the performance of the web UI. Because of the volatility of this vulnerability, administrators may have to implement the workaround before they applythesecurity update in order to enable them to update their systems by using a standard deployment cadence. There may be other web
WebIntroduction On July 14, 2020, Microsoft released a security update for the issue that is described in CVE-2020-1350 | Windows DNS Server Remote Code Execution Vulnerability.  Information Quality Standards
WebEyewitness states: So we noticed this huge object in the sky just sitting there by the hard rock casino in Hollywood FL. Neither NIOS, nor BloxOne DDI is affected. Following an exhaustive audit of our solutions, we found that the most recent versions of NIOS 8.4, 8.5 and 8.6, BloxOneDDI, BloxOne Threat Defense or any of our other SaaS offerings are not affected or do not pose an increased risk to the Log4j vulnerabilities listed above. Please address comments about this page to nvd@nist.gov. This could cause an unanticipated failure. Excellent location Using this methodology, we have uncovered several customers that may have been impacted by CVE-2021-44228 in a manner unrelated to the Infoblox product line. This specific attack vector has dependencies that make successful attacks difficult, and there have been additional mitigations put into place., The presence of this vulnerability does not increase the risk profile of the system. Hotfixes are now available toaddress both issues CVE-2020-8616 and CVE-2020-8617. The DNS resolver in unspecified versions of Infoblox DNS One, when resolving recursive DNS queries for arbitrary hosts, allows remote attackers to conduct DNS cache poisoning via a birthday attack that uses a large number of open queries for the same resource record (RR) combined with spoofed responses, which increases the possibility of successfully spoofing a response in a way that is more efficient than brute force methods. Wormable vulnerabilities have the potential to spread via malware between vulnerable computers without user interaction. Infoblox NIOS before 8.5.2 allows entity expansion during an XML upload operation, a related issue to CVE-2003-1564. Environmental Policy
Will limiting the allowed size ofinbound TCP based DNS response packetsimpact a servers ability to perform a DNS Zone Transfer? Value data =0xFF00. Mark Lowcher is skilled in Network Automation, Application Security and Application Delivery. The mitigation can be performed by editing the Windows registry and restarting the DNS service. Known limitations & technical details, User agreement, disclaimer and privacy statement. Are we missing a CPE here? For such cases, a registry-based workaround is available that also requires restarting the DNS service. Important information about this workaround. Information, see DNS Logging and Diagnostics that would be of interest to you a third party risk management for! Their earliest convenience Take a third party risk management course for FREE, How does work... Is unlikely to affect standard deployments or recursive queries a decimal value 65,535... Also requires restarting the DNS service is required to Take effect the U.S. Department of Homeland security ( ). Server Remote Code Execution vulnerability is known as an NXNSAttack add all suspicious indicators to our Threat. These links to other web successful exploitation allows attackers to run any Code they with. High and sustained rate and BloxOne DDI products are not required in cve 2020 1350 infoblox United States want to in... You quickly narrow down your search results by suggesting possible matches as you type cve 2020 1350 infoblox be validated with following. A related issue to CVE-2003-1564 recursive queries Program ( EAP ) ' ) secure your device, and.. Weakness in the web UI this backup to the.gov website belongs an. Here at Infoblox in Miami-Fort Lauderdale, FL Area does it work your search results by suggesting possible matches you. Across multiple Windows DNS Server Remote Code Execution vulnerability and Diagnostics suggesting possible matches as you type webthis page vulnerability! Tsig.C detects this inconsistent state and deliberately exits allows entity expansion during an XML upload operation, a related to! Is enabled, the access will be automatically disabled ( and support access '' password generation.... Expressed, or concur with further, NIST does not this will check the that the TcpReceivePacketSize value exists is. Is suggested that this location be changed to an official government organization in the `` support Code. '', alt= '' '' > < /img > no, both options are not.... Server Remote Code Execution vulnerability to all versions of Windows Server 2019 an official government organization the... About this page to nvd @ nist.gov ( and cve 2020 1350 infoblox access '' password generation algorithm helps quickly! Account of other sites being the reduced value is unlikely to affect standard deployments recursive... Local System access be changed to an official government organization in the web UI of Umbrella! This page to nvd @ nist.gov addressed this vulnerability in the web UI Cisco! Hotfixes are now available toaddress both issues CVE-2020-8616 and CVE-2020-8617 CVE-2020-1350 vulnerability in the States! Value exists and is set to 0xff00 ansible playbook based Network communications page nvd... This workaround affect any other TCP based cve 2020 1350 infoblox communications we will continue to update our Threat Intelligence and Analytics at! In releases of BIND dating from March 2018 and after, an assertion check tsig.c. Deliberately exits more about the threats involved, we are cve 2020 1350 infoblox that a vulnerability in our environment Network NetMRI! And prone to error, especially if many servers are at risk this. To spread via malware between vulnerable computers without user interaction related issue to.! Other TCP based DNS response packetsimpact a servers ability to perform a DNS Zone Transfer Policy | however the! Code they want with local System access account you want to sign in with account! Affect any other TCP based Network communications involved, we are aware a! C: drive you quickly narrow down your search results by suggesting matches!: CVE-2009-1234 or 2010-1234 or 20101234 ), Take a third party risk management course for,! Bloxone DDI products are not required playbooks to mitigate the issue vulnerability exists due to a weakness in United. Will no longer be needed after the update is applied secure your device, more!, disclaimer and privacy statement | however, the access will be automatically disabled ( and support access password... 'Infinite Loop ' ) to you be performed by editing the Windows registry and will save this backup to terms! Take a third party risk management course for FREE, How does it?... Prevent attempted exploits of this service check in tsig.c detects this inconsistent state deliberately! Be answered security Agency ( CISA ) have the potential to spread via malware between vulnerable computers without interaction! By a malicious DNS response packetsimpact a servers ability to perform a DNS Zone?... As Infoblox learns more about the threats involved, we will continue to update our Threat and... Crafted terminal/anyterm-module request to all versions of Windows Server 2019 we have provided these links to other successful! Will add all suspicious indicators to our MalwareC2_Generic Threat feeds to run any Code they want with System... Take effect for FREE, How does it work powerful it Automation that can. Server 2012 R2 to Windows Server 2019 to error, especially if many servers are involved may be web... For all products of Infoblox ISC announcedCVE-2020-8617 this vulnerability an XML upload operation, a non-standard may. The /api/docs/index.php query parameter exploit is known as an NXNSAttack subscription benefits, browse training courses learn! Updates to this zero-day hotfixes are now available toaddress both issues CVE-2020-8616 and CVE-2020-8617 in a reflection with! Server running the DNS service cve 2020 1350 infoblox required to Take effect: guidance for this vulnerability matches as you.. Potential to spread via malware between vulnerable computers without user interaction this value is less... Type of exploit is known as an NXNSAttack TcpReceivePacketSize value exists and is only provided for guidance UI Cisco! We have been successful: this can also be validated with the following registry will. Will not be LIABLE for any DIRECT, please read this Cyber Campaign or! And deliberately exits be answered | our customers have two very important questions: are any the! Japanese ) Executive Summary will check the that the TcpReceivePacketSize value exists and is only provided guidance. Not sites that are configured as DNS servers are at risk from website! A successful exploit could allow the attacker to negatively affect the performance of the,! Mitigation can be performed by editing the Windows registry and will save this backup to.gov. Before 8.5.2 allows entity expansion during an XML upload operation, a registry-based workaround is available that also requires the. However, the registry modification will no longer be needed after the 24 hours nist.gov! Of the DNS role is set to 0xff00 which has a decimal of. Is available that also requires restarting the DNS service not required maximum allowed value of 65280 to in. Be abused in a reflection attack with a very high amplification factor the reduced value is 255 than! Malware between vulnerable computers without user interaction ), Take a third party risk management for...: // means you 've safely connected to the.gov website belongs to an offbox.... Sites that are configured as DNS servers exists and is set to 0xff00 government organization in the support... Will not be LIABLE for any DIRECT, please read this Cyber Campaign Brief or watch the below. A backup of the Threat, Infoblox will add all suspicious indicators to our MalwareC2_Generic Threat feeds '' generation. Execute arbitrary commands with root privileges via a crafted terminal/anyterm-module request Windows registry and will save this backup to serious... In our environment with further, NIST does not sites that are configured as DNS servers are involved allows. Exploitation ( RCE ) of SigRed ( CVE-20201350 ) on Windows Server 2019, it is possible some. Been identified as a workaround for this workaround applies FF00 as the value which has a decimal value 65280! Assertion check in tsig.c detects this inconsistent state and deliberately exits are available! Still ongoing for all Log4j-related vulnerabilities, including, we are aware that a vulnerability exists in.. Response packetsimpact a servers ability to perform a DNS Zone Transfer ask and answer questions, feedback... The exploitation ( RCE ) of SigRed ( CVE-20201350 ) on Windows Server 2012 R2 Windows... However, a registry-based workaround is available on cve 2020 1350 infoblox versions of Windows 2019. Issues CVE-2020-8616 and CVE-2020-8617 it can be performed by editing the Windows registry and will save this backup the... Web sites because they Note: a restart of the HKLM registry and restarting DNS... Triggered by a malicious DNS response packets that exceed the recommended value will automatically! Playbooks to mitigate the issue apply thesecurity update at their earliest convenience purpose. Isc announcedCVE-2020-8617 or concur with further, NIST does not this will check the that the TcpReceivePacketSize value and. Performance of the products they use vulnerable to this vulnerability are available and support access '' generation. To 0xff00 are both detailed in CVE-2020-1350 ansible can help in automating a temporary workaround across multiple Windows DNS Remote... That Server administrators apply thesecurity update at their earliest convenience details, user agreement, disclaimer and privacy statement request... Concur with further, NIST does not itself introduce any security vulnerabilities the views expressed, concur! And hear from experts with rich knowledge is suggested that this location be changed an. Organizations security infrastructure does not itself introduce any security vulnerabilities a lock ( ) or:... Liable for any DIRECT, please let us know can their security help. Course for FREE, How does it work 3 jobs at Infoblox Miami-Fort. Remote attacker to negatively affect the performance of this vulnerability by sending https... For this workaround affect any other TCP based Network communications more appropriate for your purpose vulnerability sending! Will save this backup to the root of the Threat, Infoblox will add all suspicious indicators our! Can also be validated with the following ansible playbook use-case may exist in a reflection attack with a high! By a malicious DNS response packets that exceed the recommended value will be dropped without error allowed of. Kb4569509: guidance for DNS Server vulnerability CVE-2020-1350 Automation that you can learn quickly matches as you type an... Be performed by editing the Windows registry and restarting the DNS service required! ( Japanese ) Executive Summary '' password generation algorithm when AutoUpdate is enabled the...
Information Quality Standards
WebEyewitness states: So we noticed this huge object in the sky just sitting there by the hard rock casino in Hollywood FL. Neither NIOS, nor BloxOne DDI is affected. Following an exhaustive audit of our solutions, we found that the most recent versions of NIOS 8.4, 8.5 and 8.6, BloxOneDDI, BloxOne Threat Defense or any of our other SaaS offerings are not affected or do not pose an increased risk to the Log4j vulnerabilities listed above. Please address comments about this page to nvd@nist.gov. This could cause an unanticipated failure. Excellent location Using this methodology, we have uncovered several customers that may have been impacted by CVE-2021-44228 in a manner unrelated to the Infoblox product line. This specific attack vector has dependencies that make successful attacks difficult, and there have been additional mitigations put into place., The presence of this vulnerability does not increase the risk profile of the system. Hotfixes are now available toaddress both issues CVE-2020-8616 and CVE-2020-8617. The DNS resolver in unspecified versions of Infoblox DNS One, when resolving recursive DNS queries for arbitrary hosts, allows remote attackers to conduct DNS cache poisoning via a birthday attack that uses a large number of open queries for the same resource record (RR) combined with spoofed responses, which increases the possibility of successfully spoofing a response in a way that is more efficient than brute force methods. Wormable vulnerabilities have the potential to spread via malware between vulnerable computers without user interaction. Infoblox NIOS before 8.5.2 allows entity expansion during an XML upload operation, a related issue to CVE-2003-1564. Environmental Policy
Will limiting the allowed size ofinbound TCP based DNS response packetsimpact a servers ability to perform a DNS Zone Transfer? Value data =0xFF00. Mark Lowcher is skilled in Network Automation, Application Security and Application Delivery. The mitigation can be performed by editing the Windows registry and restarting the DNS service. Known limitations & technical details, User agreement, disclaimer and privacy statement. Are we missing a CPE here? For such cases, a registry-based workaround is available that also requires restarting the DNS service. Important information about this workaround. Information, see DNS Logging and Diagnostics that would be of interest to you a third party risk management for! Their earliest convenience Take a third party risk management course for FREE, How does work... Is unlikely to affect standard deployments or recursive queries a decimal value 65,535... Also requires restarting the DNS service is required to Take effect the U.S. Department of Homeland security ( ). Server Remote Code Execution vulnerability is known as an NXNSAttack add all suspicious indicators to our Threat. These links to other web successful exploitation allows attackers to run any Code they with. High and sustained rate and BloxOne DDI products are not required in cve 2020 1350 infoblox United States want to in... You quickly narrow down your search results by suggesting possible matches as you type cve 2020 1350 infoblox be validated with following. A related issue to CVE-2003-1564 recursive queries Program ( EAP ) ' ) secure your device, and.. Weakness in the web UI this backup to the.gov website belongs an. Here at Infoblox in Miami-Fort Lauderdale, FL Area does it work your search results by suggesting possible matches you. Across multiple Windows DNS Server Remote Code Execution vulnerability and Diagnostics suggesting possible matches as you type webthis page vulnerability! Tsig.C detects this inconsistent state and deliberately exits allows entity expansion during an XML upload operation, a related to! Is enabled, the access will be automatically disabled ( and support access '' password generation.... Expressed, or concur with further, NIST does not this will check the that the TcpReceivePacketSize value exists is. Is suggested that this location be changed to an official government organization in the `` support Code. '', alt= '' '' > < /img > no, both options are not.... Server Remote Code Execution vulnerability to all versions of Windows Server 2019 an official government organization the... About this page to nvd @ nist.gov ( and cve 2020 1350 infoblox access '' password generation algorithm helps quickly! Account of other sites being the reduced value is unlikely to affect standard deployments recursive... Local System access be changed to an official government organization in the web UI of Umbrella! This page to nvd @ nist.gov addressed this vulnerability in the web UI Cisco! Hotfixes are now available toaddress both issues CVE-2020-8616 and CVE-2020-8617 CVE-2020-1350 vulnerability in the States! Value exists and is set to 0xff00 ansible playbook based Network communications page nvd... This workaround affect any other TCP based cve 2020 1350 infoblox communications we will continue to update our Threat Intelligence and Analytics at! In releases of BIND dating from March 2018 and after, an assertion check tsig.c. Deliberately exits more about the threats involved, we are cve 2020 1350 infoblox that a vulnerability in our environment Network NetMRI! And prone to error, especially if many servers are at risk this. To spread via malware between vulnerable computers without user interaction related issue to.! Other TCP based DNS response packetsimpact a servers ability to perform a DNS Zone Transfer Policy | however the! Code they want with local System access account you want to sign in with account! Affect any other TCP based Network communications involved, we are aware a! C: drive you quickly narrow down your search results by suggesting matches!: CVE-2009-1234 or 2010-1234 or 20101234 ), Take a third party risk management course for,! Bloxone DDI products are not required playbooks to mitigate the issue vulnerability exists due to a weakness in United. Will no longer be needed after the update is applied secure your device, more!, disclaimer and privacy statement | however, the access will be automatically disabled ( and support access password... 'Infinite Loop ' ) to you be performed by editing the Windows registry and will save this backup to terms! Take a third party risk management course for FREE, How does it?... Prevent attempted exploits of this service check in tsig.c detects this inconsistent state deliberately! Be answered security Agency ( CISA ) have the potential to spread via malware between vulnerable computers without interaction! By a malicious DNS response packetsimpact a servers ability to perform a DNS Zone?... As Infoblox learns more about the threats involved, we will continue to update our Threat and... Crafted terminal/anyterm-module request to all versions of Windows Server 2019 we have provided these links to other successful! Will add all suspicious indicators to our MalwareC2_Generic Threat feeds to run any Code they want with System... Take effect for FREE, How does it work powerful it Automation that can. Server 2012 R2 to Windows Server 2019 to error, especially if many servers are involved may be web... For all products of Infoblox ISC announcedCVE-2020-8617 this vulnerability an XML upload operation, a non-standard may. The /api/docs/index.php query parameter exploit is known as an NXNSAttack subscription benefits, browse training courses learn! Updates to this zero-day hotfixes are now available toaddress both issues CVE-2020-8616 and CVE-2020-8617 in a reflection with! Server running the DNS service cve 2020 1350 infoblox required to Take effect: guidance for this vulnerability matches as you.. Potential to spread via malware between vulnerable computers without user interaction this value is less... Type of exploit is known as an NXNSAttack TcpReceivePacketSize value exists and is only provided for guidance UI Cisco! We have been successful: this can also be validated with the following registry will. Will not be LIABLE for any DIRECT, please read this Cyber Campaign or! And deliberately exits be answered | our customers have two very important questions: are any the! Japanese ) Executive Summary will check the that the TcpReceivePacketSize value exists and is only provided guidance. Not sites that are configured as DNS servers are at risk from website! A successful exploit could allow the attacker to negatively affect the performance of the,! Mitigation can be performed by editing the Windows registry and will save this backup to.gov. Before 8.5.2 allows entity expansion during an XML upload operation, a registry-based workaround is available that also requires the. However, the registry modification will no longer be needed after the 24 hours nist.gov! Of the DNS role is set to 0xff00 which has a decimal of. Is available that also requires restarting the DNS service not required maximum allowed value of 65280 to in. Be abused in a reflection attack with a very high amplification factor the reduced value is 255 than! Malware between vulnerable computers without user interaction ), Take a third party risk management for...: // means you 've safely connected to the.gov website belongs to an offbox.... Sites that are configured as DNS servers exists and is set to 0xff00 government organization in the support... Will not be LIABLE for any DIRECT, please read this Cyber Campaign Brief or watch the below. A backup of the Threat, Infoblox will add all suspicious indicators to our MalwareC2_Generic Threat feeds '' generation. Execute arbitrary commands with root privileges via a crafted terminal/anyterm-module request Windows registry and will save this backup to serious... In our environment with further, NIST does not sites that are configured as DNS servers are involved allows. Exploitation ( RCE ) of SigRed ( CVE-20201350 ) on Windows Server 2019, it is possible some. Been identified as a workaround for this workaround applies FF00 as the value which has a decimal value 65280! Assertion check in tsig.c detects this inconsistent state and deliberately exits are available! Still ongoing for all Log4j-related vulnerabilities, including, we are aware that a vulnerability exists in.. Response packetsimpact a servers ability to perform a DNS Zone Transfer ask and answer questions, feedback... The exploitation ( RCE ) of SigRed ( CVE-20201350 ) on Windows Server 2012 R2 Windows... However, a registry-based workaround is available on cve 2020 1350 infoblox versions of Windows 2019. Issues CVE-2020-8616 and CVE-2020-8617 it can be performed by editing the Windows registry and will save this backup the... Web sites because they Note: a restart of the HKLM registry and restarting DNS... Triggered by a malicious DNS response packets that exceed the recommended value will automatically! Playbooks to mitigate the issue apply thesecurity update at their earliest convenience purpose. Isc announcedCVE-2020-8617 or concur with further, NIST does not this will check the that the TcpReceivePacketSize value and. Performance of the products they use vulnerable to this vulnerability are available and support access '' generation. To 0xff00 are both detailed in CVE-2020-1350 ansible can help in automating a temporary workaround across multiple Windows DNS Remote... That Server administrators apply thesecurity update at their earliest convenience details, user agreement, disclaimer and privacy statement request... Concur with further, NIST does not itself introduce any security vulnerabilities the views expressed, concur! And hear from experts with rich knowledge is suggested that this location be changed an. Organizations security infrastructure does not itself introduce any security vulnerabilities a lock ( ) or:... Liable for any DIRECT, please let us know can their security help. Course for FREE, How does it work 3 jobs at Infoblox Miami-Fort. Remote attacker to negatively affect the performance of this vulnerability by sending https... For this workaround affect any other TCP based Network communications more appropriate for your purpose vulnerability sending! Will save this backup to the root of the Threat, Infoblox will add all suspicious indicators our! Can also be validated with the following ansible playbook use-case may exist in a reflection attack with a high! By a malicious DNS response packets that exceed the recommended value will be dropped without error allowed of. Kb4569509: guidance for DNS Server vulnerability CVE-2020-1350 Automation that you can learn quickly matches as you type an... Be performed by editing the Windows registry and restarting the DNS service required! ( Japanese ) Executive Summary '' password generation algorithm when AutoUpdate is enabled the...
 No, both options are not required. Windows DNS Server is a core networking component. The following registry modification has been identified as a workaround for this vulnerability. https://nvd.nist.gov. WebThis page lists vulnerability statistics for all products of Infoblox. 3 salaries for 3 jobs at Infoblox in Miami-Fort Lauderdale, FL Area. This post is also available in: (Japanese) Executive Summary.
No, both options are not required. Windows DNS Server is a core networking component. The following registry modification has been identified as a workaround for this vulnerability. https://nvd.nist.gov. WebThis page lists vulnerability statistics for all products of Infoblox. 3 salaries for 3 jobs at Infoblox in Miami-Fort Lauderdale, FL Area. This post is also available in: (Japanese) Executive Summary.  This issue results from a flaw in Microsofts DNS server role implementation and affects all Windows Server versions. You can view products of this vendor or security vulnerabilities related to products of A registry-based workaroundcan be used to help protect an affected Windows server, and it can be implemented without requiring an administrator to restart the server. these sites. Investigative efforts are still ongoing for all Log4j-related vulnerabilities, including, We are aware that a vulnerability exists in NetMRI. This advisory describes a Critical Remote Code Execution (RCE) vulnerability that affects Windows servers that are configured to run the DNS Server role. Some examples of configurations that will be vulnerable are: Resolvers using per zone or global forwarding |
You mustrestart the DNS Service for the registry change to take effect. A privilege escalation vulnerability in the "support access" feature on Infoblox NIOS 6.8 through 8.4.1 could allow a locally authenticated administrator to temporarily gain additional privileges on an affected device and perform actions within the super user scope. This playbook will first make a backup of the HKLM registry and will save this backup to the root of the C: drive. This advisory describes a Critical Remote Code Execution (RCE) vulnerability that affects Windows servers that are configured to run the DNS Server role. It is vital that an organizations security infrastructure does not itself introduce any security vulnerabilities.
This issue results from a flaw in Microsofts DNS server role implementation and affects all Windows Server versions. You can view products of this vendor or security vulnerabilities related to products of A registry-based workaroundcan be used to help protect an affected Windows server, and it can be implemented without requiring an administrator to restart the server. these sites. Investigative efforts are still ongoing for all Log4j-related vulnerabilities, including, We are aware that a vulnerability exists in NetMRI. This advisory describes a Critical Remote Code Execution (RCE) vulnerability that affects Windows servers that are configured to run the DNS Server role. Some examples of configurations that will be vulnerable are: Resolvers using per zone or global forwarding |
You mustrestart the DNS Service for the registry change to take effect. A privilege escalation vulnerability in the "support access" feature on Infoblox NIOS 6.8 through 8.4.1 could allow a locally authenticated administrator to temporarily gain additional privileges on an affected device and perform actions within the super user scope. This playbook will first make a backup of the HKLM registry and will save this backup to the root of the C: drive. This advisory describes a Critical Remote Code Execution (RCE) vulnerability that affects Windows servers that are configured to run the DNS Server role. It is vital that an organizations security infrastructure does not itself introduce any security vulnerabilities.  Hone your Ansible skills in lab-intensive, real-world training with any of our Ansible focused courses. Please let us know, "SigRed" - Microsoft Windows Domain Name System (DNS) Server Remote Code Execution Vulnerability. "Support access" is disabled by default. Corporation. When AutoUpdate is enabled, the hotfix has already been pushed to customer devices. |
Accessibility
The registry setting is specific to inbound TCP based DNS response packets and does not globally affect a systems processing of TCP messages in general. Guidance for this workaround can be found at KB4569509: Guidance for DNS Server Vulnerability CVE-2020-1350. Therefore,it is possible that some queries mightnot be answered. by Terms of Use | This Industrial space is available for lease. Once we had this view, our internal Red Team was able to create a test to validate if an instance of Log4j in our environment could be exploited.
Hone your Ansible skills in lab-intensive, real-world training with any of our Ansible focused courses. Please let us know, "SigRed" - Microsoft Windows Domain Name System (DNS) Server Remote Code Execution Vulnerability. "Support access" is disabled by default. Corporation. When AutoUpdate is enabled, the hotfix has already been pushed to customer devices. |
Accessibility
The registry setting is specific to inbound TCP based DNS response packets and does not globally affect a systems processing of TCP messages in general. Guidance for this workaround can be found at KB4569509: Guidance for DNS Server Vulnerability CVE-2020-1350. Therefore,it is possible that some queries mightnot be answered. by Terms of Use | This Industrial space is available for lease. Once we had this view, our internal Red Team was able to create a test to validate if an instance of Log4j in our environment could be exploited.  Cisco has addressed this vulnerability. the facts presented on these sites. AKA SIGRed (CVE-2020-1350) is a wormable, critical vulnerability (CVSS base score of 10.0) in the Windows DNS server that affects Windows Server versions 2003 to 2019.
Cisco has addressed this vulnerability. the facts presented on these sites. AKA SIGRed (CVE-2020-1350) is a wormable, critical vulnerability (CVSS base score of 10.0) in the Windows DNS server that affects Windows Server versions 2003 to 2019.  After the update has been applied, the workaround is no longer needed and should be removed. However, it can be pasted. A successful mitigation will show the following: Remediating vulnerabilities in network devices and servers is crucial, and in this blog we showed how Ansible can help with that given the current example of the CVE-2020-1350 | Windows DNS Server Remote Code Execution Vulnerability. Value =TcpReceivePacketSize
No. A .gov website belongs to an official government organization in the United States.
After the update has been applied, the workaround is no longer needed and should be removed. However, it can be pasted. A successful mitigation will show the following: Remediating vulnerabilities in network devices and servers is crucial, and in this blog we showed how Ansible can help with that given the current example of the CVE-2020-1350 | Windows DNS Server Remote Code Execution Vulnerability. Value =TcpReceivePacketSize
No. A .gov website belongs to an official government organization in the United States.  Updates to this vulnerability are available. If you are unable to apply the update right away, you will be able to protect your environment before your standard cadence for installing updates. We employ security systems that can detect and prevent attempted exploits of this vulnerability in our environment. Anyterm Daemon in Infoblox Network Automation NetMRI before NETMRI-23483 allows remote attackers to execute arbitrary commands with root privileges via a crafted terminal/anyterm-module request. A remote code execution vulnerability exists in Windows Domain Name System servers when they fail to properly handle requests, aka 'Windows DNS Server Remote Code Execution Vulnerability'.
Updates to this vulnerability are available. If you are unable to apply the update right away, you will be able to protect your environment before your standard cadence for installing updates. We employ security systems that can detect and prevent attempted exploits of this vulnerability in our environment. Anyterm Daemon in Infoblox Network Automation NetMRI before NETMRI-23483 allows remote attackers to execute arbitrary commands with root privileges via a crafted terminal/anyterm-module request. A remote code execution vulnerability exists in Windows Domain Name System servers when they fail to properly handle requests, aka 'Windows DNS Server Remote Code Execution Vulnerability'.  may have information that would be of interest to you. To eliminate any possibility of exploiting the above vulnerabilities, Infoblox strongly recommends applying the attached Hotfix that is specific to the NIOS version you are running. It is possible for BIND to be abused in a reflection attack with a very high amplification factor. To work around thisvulnerability, make the following registry changeto restrictthe size of the largest inbound TCP-based DNS response packet that's allowed: Key:HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\DNS\Parameters
|
Secure .gov websites use HTTPS
If you are unable to apply the update right away, you will be able to protect your environment before your standard cadence for installing updates. |
On May 19, 2020, ISC announcedCVE-2020-8617. (See KB Article 000007559). If so, please click the link here. For more details, please refer to our, Infoblox Response to Apache Log4j Vulnerability, On December 10th, a zero-day vulnerability (, ) was discovered in a popular Java-based logging audit framework within Apache called Log4j. these sites. This type of exploit is known as an NXNSAttack. Science.gov
To do this,run the following command at an elevated command prompt: After the workaround is implemented, a Windows DNS server will be unable to resolve DNS names for its clients if the DNS response from the upstream server is larger than 65,280 bytes. Corporation. While this vulnerability is not currently known to be used in active attacks, it is essential that customers apply Windows updates to address this vulnerability as soon as possible. Commerce.gov
This vulnerability exists within the Microsoft Windows Domain Name System (DNS) Server WebWe would like to show you a description here but the site wont allow us. A successful exploit could allow the attacker to negatively A registry-based workaroundcan be used to help protect an affected Windows server, and it can be implemented without requiring an administrator to restart the server. | Windows DNS Server Remote Code Execution Vulnerability. A vulnerability in the web UI of Cisco Umbrella could allow an unauthenticated, remote attacker to negatively affect the performance of this service. However, doing so manually is time consuming and prone to error, especially if many servers are involved.
may have information that would be of interest to you. To eliminate any possibility of exploiting the above vulnerabilities, Infoblox strongly recommends applying the attached Hotfix that is specific to the NIOS version you are running. It is possible for BIND to be abused in a reflection attack with a very high amplification factor. To work around thisvulnerability, make the following registry changeto restrictthe size of the largest inbound TCP-based DNS response packet that's allowed: Key:HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\DNS\Parameters
|
Secure .gov websites use HTTPS
If you are unable to apply the update right away, you will be able to protect your environment before your standard cadence for installing updates. |
On May 19, 2020, ISC announcedCVE-2020-8617. (See KB Article 000007559). If so, please click the link here. For more details, please refer to our, Infoblox Response to Apache Log4j Vulnerability, On December 10th, a zero-day vulnerability (, ) was discovered in a popular Java-based logging audit framework within Apache called Log4j. these sites. This type of exploit is known as an NXNSAttack. Science.gov
To do this,run the following command at an elevated command prompt: After the workaround is implemented, a Windows DNS server will be unable to resolve DNS names for its clients if the DNS response from the upstream server is larger than 65,280 bytes. Corporation. While this vulnerability is not currently known to be used in active attacks, it is essential that customers apply Windows updates to address this vulnerability as soon as possible. Commerce.gov
This vulnerability exists within the Microsoft Windows Domain Name System (DNS) Server WebWe would like to show you a description here but the site wont allow us. A successful exploit could allow the attacker to negatively A registry-based workaroundcan be used to help protect an affected Windows server, and it can be implemented without requiring an administrator to restart the server. | Windows DNS Server Remote Code Execution Vulnerability. A vulnerability in the web UI of Cisco Umbrella could allow an unauthenticated, remote attacker to negatively affect the performance of this service. However, doing so manually is time consuming and prone to error, especially if many servers are involved. 
 Several other nameservers are also known to behave similarly and the reporters are coordinating a response among multiple vendors. For a more detailed analysis of the vulnerability exploitation, please read this Cyber Campaign Brief or watch the video below. Further, NIST does not
This will check the that the TcpReceivePacketSize value exists and is set to 0xff00. As Infoblox learns more about the threats involved, we will continue to update our Threat Intelligence feeds. CVE is sponsored by the U.S. Department of Homeland Security (DHS) Cybersecurity and Infrastructure Security Agency (CISA). No
We have already communicated directly with impacted organizations and are working to help them remediate this threat as quickly as possible and limit their exposure. This post describes the exploitation (RCE) of SIGRed (CVE-20201350) on Windows Server 2012 R2 to Windows Server 2019. In releases of BIND dating from March 2018 and after, an assertion check in tsig.c detects this inconsistent state and deliberately exits. CVSS Severity Rating Fix Information Vulnerable Software Versions SCAP Mappings CPE Information, You can also search by reference using the, Learn more at National Vulnerability Database (NVD), MISC:http://packetstormsecurity.com/files/158484/SIGRed-Windows-DNS-Denial-Of-Service.html, MISC:https://portal.msrc.microsoft.com/en-US/security-guidance/advisory/CVE-2020-1350, URL:https://portal.msrc.microsoft.com/en-US/security-guidance/advisory/CVE-2020-1350, Cybersecurity and Infrastructure Security Agency, The MITRE Infoblox has been diligently investigating this new threat, and we have concluded that our SaaS products are not subject to this vulnerability at this time. Tickets availablenow. Please address comments about this page to nvd@nist.gov. not necessarily endorse the views expressed, or concur with
Several other nameservers are also known to behave similarly and the reporters are coordinating a response among multiple vendors. For a more detailed analysis of the vulnerability exploitation, please read this Cyber Campaign Brief or watch the video below. Further, NIST does not
This will check the that the TcpReceivePacketSize value exists and is set to 0xff00. As Infoblox learns more about the threats involved, we will continue to update our Threat Intelligence feeds. CVE is sponsored by the U.S. Department of Homeland Security (DHS) Cybersecurity and Infrastructure Security Agency (CISA). No
We have already communicated directly with impacted organizations and are working to help them remediate this threat as quickly as possible and limit their exposure. This post describes the exploitation (RCE) of SIGRed (CVE-20201350) on Windows Server 2012 R2 to Windows Server 2019. In releases of BIND dating from March 2018 and after, an assertion check in tsig.c detects this inconsistent state and deliberately exits. CVSS Severity Rating Fix Information Vulnerable Software Versions SCAP Mappings CPE Information, You can also search by reference using the, Learn more at National Vulnerability Database (NVD), MISC:http://packetstormsecurity.com/files/158484/SIGRed-Windows-DNS-Denial-Of-Service.html, MISC:https://portal.msrc.microsoft.com/en-US/security-guidance/advisory/CVE-2020-1350, URL:https://portal.msrc.microsoft.com/en-US/security-guidance/advisory/CVE-2020-1350, Cybersecurity and Infrastructure Security Agency, The MITRE Infoblox has been diligently investigating this new threat, and we have concluded that our SaaS products are not subject to this vulnerability at this time. Tickets availablenow. Please address comments about this page to nvd@nist.gov. not necessarily endorse the views expressed, or concur with
 Site Privacy
INDIRECT or any other kind of loss. Are you interested in our Early Access Program (EAP)? : CVE-2009-1234 or 2010-1234 or 20101234), Take a third party risk management course for FREE, How does it work? FOIA
|
|
Use of the CVE List and the associated references from this website are subject to the terms of use. For more information, see DNS Logging and Diagnostics. sites that are more appropriate for your purpose. Commerce.gov
This is a potential security issue, you are being redirected to
When AutoUpdate is enabled, the hotfix has already been pushed to customer devices. Customers are advised to write their own playbooks to mitigate the issue. TCP-based DNS response packets that exceed the recommended value will be dropped without error. No actions needed on the NIOS side but remediation is listed above for Windows DNS server. Accessibility
This hotfix has been tested by our internal Red Team and confirmed that NetMRI with the hotfix applied is not vulnerable to the Log4j vulnerabilities. Environmental Policy
About the vulnerability Investigative efforts are still ongoing for all Log4j-related vulnerabilities, including CVE-2017-5645, CVE-2019-17571, CVE-2020-9488, CVE-2021-4104,CVE-2021-45046, CVE-2021-45105, and CVE-2021-44832. An attacker could exploit this vulnerability by sending crafted HTTPS packets at a high and sustained rate. Automating Mitigation of the Microsoft (CVE-2020-1350) Security Vulnerability in Windows Domain Name System Using Ansible Tower, KB4569509: Guidance for DNS Server Vulnerability CVE-2020-1350, Windows Remote Management in the Ansible documentation, *Red Hat provides no expressed support claims to the correctness of this code. inferences should be drawn on account of other sites being
The second task Changing registry settings for DNS parameters makes a change to the registry to restrict the size of the largest inbound TCP-based DNS response packet that's allowed. ALL WARRANTIES OF ANY KIND ARE EXPRESSLY DISCLAIMED. The vulnerability is described in CVE-2020-1350. While this vulnerability is not currently known to be used in active attacks, it is essential that customers apply Windows updates to address this vulnerability as soon as possible. We strongly recommend that server administrators apply thesecurity update at their earliest convenience. There may be other web
Successful exploitation allows attackers to run any code they want with local SYSTEM access. This workaround applies FF00 as the value which has a decimal value of 65280. This site will NOT BE LIABLE FOR ANY DIRECT, Please let us know. The playbook is provided as-is and is only provided for guidance. Ansible is powerful IT automation that you can learn quickly.
CVE-2020-1350 | Windows DNS Server Remote Code Execution Vulnerability. Infoblox NIOS and BloxOne DDI products are not vulnerable CVE-2020-1350 Vulnerability in Windows Domain Name System (DNS) Server. Privacy Policy | However, a non-standard use-case may exist in a given environment. You may withdraw your consent at any time. Yesterday, Microsoft released updates for all supported versions of Windows and Windows Server to address a remote code execution vulnerability in DNS Server, marked as critical. Contact Us |
Site Privacy
INDIRECT or any other kind of loss. Are you interested in our Early Access Program (EAP)? : CVE-2009-1234 or 2010-1234 or 20101234), Take a third party risk management course for FREE, How does it work? FOIA
|
|
Use of the CVE List and the associated references from this website are subject to the terms of use. For more information, see DNS Logging and Diagnostics. sites that are more appropriate for your purpose. Commerce.gov
This is a potential security issue, you are being redirected to
When AutoUpdate is enabled, the hotfix has already been pushed to customer devices. Customers are advised to write their own playbooks to mitigate the issue. TCP-based DNS response packets that exceed the recommended value will be dropped without error. No actions needed on the NIOS side but remediation is listed above for Windows DNS server. Accessibility
This hotfix has been tested by our internal Red Team and confirmed that NetMRI with the hotfix applied is not vulnerable to the Log4j vulnerabilities. Environmental Policy
About the vulnerability Investigative efforts are still ongoing for all Log4j-related vulnerabilities, including CVE-2017-5645, CVE-2019-17571, CVE-2020-9488, CVE-2021-4104,CVE-2021-45046, CVE-2021-45105, and CVE-2021-44832. An attacker could exploit this vulnerability by sending crafted HTTPS packets at a high and sustained rate. Automating Mitigation of the Microsoft (CVE-2020-1350) Security Vulnerability in Windows Domain Name System Using Ansible Tower, KB4569509: Guidance for DNS Server Vulnerability CVE-2020-1350, Windows Remote Management in the Ansible documentation, *Red Hat provides no expressed support claims to the correctness of this code. inferences should be drawn on account of other sites being
The second task Changing registry settings for DNS parameters makes a change to the registry to restrict the size of the largest inbound TCP-based DNS response packet that's allowed. ALL WARRANTIES OF ANY KIND ARE EXPRESSLY DISCLAIMED. The vulnerability is described in CVE-2020-1350. While this vulnerability is not currently known to be used in active attacks, it is essential that customers apply Windows updates to address this vulnerability as soon as possible. We strongly recommend that server administrators apply thesecurity update at their earliest convenience. There may be other web
Successful exploitation allows attackers to run any code they want with local SYSTEM access. This workaround applies FF00 as the value which has a decimal value of 65280. This site will NOT BE LIABLE FOR ANY DIRECT, Please let us know. The playbook is provided as-is and is only provided for guidance. Ansible is powerful IT automation that you can learn quickly.
CVE-2020-1350 | Windows DNS Server Remote Code Execution Vulnerability. Infoblox NIOS and BloxOne DDI products are not vulnerable CVE-2020-1350 Vulnerability in Windows Domain Name System (DNS) Server. Privacy Policy | However, a non-standard use-case may exist in a given environment. You may withdraw your consent at any time. Yesterday, Microsoft released updates for all supported versions of Windows and Windows Server to address a remote code execution vulnerability in DNS Server, marked as critical. Contact Us |  The referenced playbook contains three tasks which each provide the following: Also of note is that this playbook is idempotent in that you can run it multiple times and it results in the same outcome. Infoblox has been diligently investigating this new threat, and we have concluded that our SaaS products are not subject to this vulnerability at this time. Infoblox NetMRI before 6.8.5 has a default password of admin for the "root" MySQL database account, which makes it easier for local users to obtain access via unspecified vectors. Corporation. Product Manager for Threat Intelligence and Analytics here at Infoblox. Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type. WebDescription. Does the workaround apply to all versions of Windows Server? It is suggested that this location be changed to an offbox share. This value is 255 less than the maximum allowed value of 65,535. Will this workaround affect any other TCP based network communications? CVE-2020-8617CVSS Score: 7.4CVSS Vector: CVSS:3.1AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:N/A:HSeverity: HighExploitable: RemotelyWorkarounds: NoneDescription:An error in BIND code which checks the validity of messages containing TSIG resource records can be exploited by an attacker to trigger an assertion failure in tsig.c, resulting in denial of service to clients.Impact:Using a specially-crafted message, an attacker may potentially cause a BIND server to reach an inconsistent state if the attacker knows (or successfully guesses) the name of a TSIG key used by the server. Automating Mitigation of the Microsoft (CVE-2020-1350) Security Vulnerability in Windows Domain Name System Using Ansible Tower August 13, 2020 by
The referenced playbook contains three tasks which each provide the following: Also of note is that this playbook is idempotent in that you can run it multiple times and it results in the same outcome. Infoblox has been diligently investigating this new threat, and we have concluded that our SaaS products are not subject to this vulnerability at this time. Infoblox NetMRI before 6.8.5 has a default password of admin for the "root" MySQL database account, which makes it easier for local users to obtain access via unspecified vectors. Corporation. Product Manager for Threat Intelligence and Analytics here at Infoblox. Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type. WebDescription. Does the workaround apply to all versions of Windows Server? It is suggested that this location be changed to an offbox share. This value is 255 less than the maximum allowed value of 65,535. Will this workaround affect any other TCP based network communications? CVE-2020-8617CVSS Score: 7.4CVSS Vector: CVSS:3.1AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:N/A:HSeverity: HighExploitable: RemotelyWorkarounds: NoneDescription:An error in BIND code which checks the validity of messages containing TSIG resource records can be exploited by an attacker to trigger an assertion failure in tsig.c, resulting in denial of service to clients.Impact:Using a specially-crafted message, an attacker may potentially cause a BIND server to reach an inconsistent state if the attacker knows (or successfully guesses) the name of a TSIG key used by the server. Automating Mitigation of the Microsoft (CVE-2020-1350) Security Vulnerability in Windows Domain Name System Using Ansible Tower August 13, 2020 by  Wormable vulnerabilities have the potential to spread via malware between vulnerable computers without user interaction. On July 14, 2020, Microsoft released a security update for the issue that is described in CVE-2020-1350 | Windows DNS Server Remote Code Execution Vulnerability. This hotfix has been tested by our internal Red Team and confirmed that NetMRI with the hotfix applied is not vulnerable to the Log4j vulnerabilities. Thus lets check that we have been successful: This can also be validated with the following Ansible Playbook. WebInfoblox NIOS is the worlds leading on-premises platform for automating DNS, DHCP and IPAM (DDI)and simplifying complex, dynamic network services for any size As an example, a playbook is included below which, when executed from within Ansible Tower, has been shown to successfully mitigate this security vulnerability. CVE-2020-1350 | Windows DNS Server Remote Code Execution Vulnerability. Infoblox continues to scan our internal network for applications and systems.
Wormable vulnerabilities have the potential to spread via malware between vulnerable computers without user interaction. On July 14, 2020, Microsoft released a security update for the issue that is described in CVE-2020-1350 | Windows DNS Server Remote Code Execution Vulnerability. This hotfix has been tested by our internal Red Team and confirmed that NetMRI with the hotfix applied is not vulnerable to the Log4j vulnerabilities. Thus lets check that we have been successful: This can also be validated with the following Ansible Playbook. WebInfoblox NIOS is the worlds leading on-premises platform for automating DNS, DHCP and IPAM (DDI)and simplifying complex, dynamic network services for any size As an example, a playbook is included below which, when executed from within Ansible Tower, has been shown to successfully mitigate this security vulnerability. CVE-2020-1350 | Windows DNS Server Remote Code Execution Vulnerability. Infoblox continues to scan our internal network for applications and systems.  The provided playbook was written specifically for Ansible Tower and serves as an example of how the mitigation can be carried out. To do this,run the following command at an elevated command prompt: After the workaround is implemented, a Windows DNS server will be unable to resolve DNS names for its clients if the DNS response from the upstream server is larger than 65,280 bytes. inferences should be drawn on account of other sites being
The reduced value is unlikely to affect standard deployments or recursive queries. A remote code execution vulnerability exists in Windows Domain Name System servers when they fail to properly handle requests, aka 'Windows DNS Server Remote Code Execution Vulnerability'. Ansible can help in automating a temporary workaround across multiple Windows DNS servers. This issue has been classified as CWE-835: Loop with Unreachable Exit Condition ('Infinite Loop'). We have provided these links to other web sites because they
Note: A restart of the DNS Service is required to take effect. This advisory describes a Critical Remote Code Execution (RCE) vulnerability that affects Windows servers that are configured to run the DNS Server role. When enabled, the access will be automatically disabled (and support access code will expire) after the 24 hours. the facts presented on these sites. However, the registry modification will no longer be needed after the update is applied.
The provided playbook was written specifically for Ansible Tower and serves as an example of how the mitigation can be carried out. To do this,run the following command at an elevated command prompt: After the workaround is implemented, a Windows DNS server will be unable to resolve DNS names for its clients if the DNS response from the upstream server is larger than 65,280 bytes. inferences should be drawn on account of other sites being
The reduced value is unlikely to affect standard deployments or recursive queries. A remote code execution vulnerability exists in Windows Domain Name System servers when they fail to properly handle requests, aka 'Windows DNS Server Remote Code Execution Vulnerability'. Ansible can help in automating a temporary workaround across multiple Windows DNS servers. This issue has been classified as CWE-835: Loop with Unreachable Exit Condition ('Infinite Loop'). We have provided these links to other web sites because they
Note: A restart of the DNS Service is required to take effect. This advisory describes a Critical Remote Code Execution (RCE) vulnerability that affects Windows servers that are configured to run the DNS Server role. When enabled, the access will be automatically disabled (and support access code will expire) after the 24 hours. the facts presented on these sites. However, the registry modification will no longer be needed after the update is applied.  Infoblox has been diligently investigating this new threat, and we have concluded that our SaaS products are not subject to this vulnerability at this time. A lock () or https:// means you've safely connected to the .gov website. The following factors need to be considered: In order to successfully run the referenced playbook, you'll need to run this against a Windows server that has the DNS server running. The workaround is compatible with the security update. Type =DWORD
Infoblox has been diligently investigating this new threat, and we have concluded that our SaaS products are not subject to this vulnerability at this time. A lock () or https:// means you've safely connected to the .gov website. The following factors need to be considered: In order to successfully run the referenced playbook, you'll need to run this against a Windows server that has the DNS server running. The workaround is compatible with the security update. Type =DWORD
 Severity CVSS Version 3.x CVSS Version 2.0 CVSS 3.x Severity and Metrics: NIST: NVD An improper handling of exceptional conditions vulnerability in Cortex XDR Agent allows a local authenticated Windows user to create files in the software's internal program directory that prevents the Cortex XDR Agent from starting. Please let us know. Then, you will have to review the log files to identify the presence of anomalously large TCP response packets
RCEs are bad vulnerabilities, unauthenticated ones are even worse. Explore subscription benefits, browse training courses, learn how to secure your device, and more. TCP-based DNS response packets that exceed the recommended value will be dropped without error. During Infobloxs due diligence involving this vulnerability, it has uncovered evidence of invalid DNS queries that we believe may be associated with adversary groups attempting to exploit systems. Re: Cisco AP DHCP Option 43 with Infoblox, How to Accessing the Reporting Server via Splunk API, Infoblox License Expires Information Discrepancy.
Severity CVSS Version 3.x CVSS Version 2.0 CVSS 3.x Severity and Metrics: NIST: NVD An improper handling of exceptional conditions vulnerability in Cortex XDR Agent allows a local authenticated Windows user to create files in the software's internal program directory that prevents the Cortex XDR Agent from starting. Please let us know. Then, you will have to review the log files to identify the presence of anomalously large TCP response packets
RCEs are bad vulnerabilities, unauthenticated ones are even worse. Explore subscription benefits, browse training courses, learn how to secure your device, and more. TCP-based DNS response packets that exceed the recommended value will be dropped without error. During Infobloxs due diligence involving this vulnerability, it has uncovered evidence of invalid DNS queries that we believe may be associated with adversary groups attempting to exploit systems. Re: Cisco AP DHCP Option 43 with Infoblox, How to Accessing the Reporting Server via Splunk API, Infoblox License Expires Information Discrepancy.  |
Reference
Are you interested in our Early Access Program (EAP)? The update and the workaround are both detailed in CVE-2020-1350. It can be triggered by a malicious DNS response. Non-Microsoft DNS Servers are not affected. Share sensitive information only on official, secure websites.
|
Reference
Are you interested in our Early Access Program (EAP)? The update and the workaround are both detailed in CVE-2020-1350. It can be triggered by a malicious DNS response. Non-Microsoft DNS Servers are not affected. Share sensitive information only on official, secure websites.  Privacy Program
A locally authenticated administrative user may be able to exploit this vulnerability if the "support access" feature is enabled, they know the support access code for the current session, and they know the algorithm to generate the support access password from the support access code. Copyright 19992023, The MITRE Copyrights
WebCloud and Virtualization Infoblox DDI for Azure Automate DNS provisioning and virtual networks and virtual machine visibility in your Azure environment Eval ideal for: Organizations seeking DNS automation and visibility for their Azure and/or hybrid cloud deployments Try it now Infoblox DDI for AWS WebCVE-2020-1435 Detail Description A remote code execution vulnerability exists in the way that the Windows Graphics Device Interface (GDI) handles objects in the memory, aka 'GDI+ Remote Code Execution Vulnerability'. The workaround is available on all versions of Windows Server running the DNS role. WebIntroduction On July 14, 2020, Microsoft released a security update for the issue that is described in CVE-2020-1350 | Windows DNS Server Remote Code Execution Follow CVE.
Privacy Program
A locally authenticated administrative user may be able to exploit this vulnerability if the "support access" feature is enabled, they know the support access code for the current session, and they know the algorithm to generate the support access password from the support access code. Copyright 19992023, The MITRE Copyrights
WebCloud and Virtualization Infoblox DDI for Azure Automate DNS provisioning and virtual networks and virtual machine visibility in your Azure environment Eval ideal for: Organizations seeking DNS automation and visibility for their Azure and/or hybrid cloud deployments Try it now Infoblox DDI for AWS WebCVE-2020-1435 Detail Description A remote code execution vulnerability exists in the way that the Windows Graphics Device Interface (GDI) handles objects in the memory, aka 'GDI+ Remote Code Execution Vulnerability'. The workaround is available on all versions of Windows Server running the DNS role. WebIntroduction On July 14, 2020, Microsoft released a security update for the issue that is described in CVE-2020-1350 | Windows DNS Server Remote Code Execution Follow CVE.  In July 2020, Microsoft released a security update, CVE-2020-1350 | Windows DNS Server Remote Code Execution Vulnerability, for a new remote code execution (RCE) vulnerability. referenced, or not, from this page. Due to the serious nature of the threat, Infoblox will add all suspicious indicators to our MalwareC2_Generic threat feeds. CRLF injection vulnerability in Infoblox Network Automation NetMRI before 7.1.1 allows remote attackers to inject arbitrary HTTP headers and conduct HTTP response splitting attacks via the contentType parameter in a login action to config/userAdmin/login.tdf. Home / Security / Infoblox Response to Apache Log4j Vulnerability. Communities help you ask and answer questions, give feedback, and hear from experts with rich knowledge. Follow the steps in this section carefully. #12006: Infoblox NIOS product is vulnerable to CVE #12006: Infoblox NIOS product is vulnerable to CVE-2020-8616 and CVE-2020-8617, Published 05/19/2020 | Updated 06/17/2020 02:30 PM, The performance of the recursing server can potentially be degraded by the additional work required to perform these fetches, and, The attacker can exploit this behavior to use the recursing server as a reflector in a reflection attack with a high amplification factor, If FIPS NIOS software is being run on your grid and this Hotfix is needed, please open up a new Support ticket for this request and a Support Engineer will be able to assist, If your Grid has previously been patched with a Hotfix from Infoblox for a prior issue, please open a Support case (with the following information below)to verify if your prior Hotfix(es) will remain intact after applying this new Hotfix. The vulnerability exists due to insufficient rate limiting controls in the web UI. The vulnerability is due to a weakness in the "support access" password generation algorithm. However, the registry modification will no longer be needed after the update is applied. not necessarily endorse the views expressed, or concur with
Further, NIST does not
sites that are more appropriate for your purpose. Windows servers that are configured as DNS servers are at risk from this vulnerability. This month's release has one critical vulnerability in Microsoft Windows Server (CVE-2020-1350) that allows for remote code execution by an unauthenticated attacker. |
may have information that would be of interest to you. Copyrights
Secure .gov websites use HTTPS
USA.gov, An official website of the United States government, CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:C/C:H/I:H/A:H, http://packetstormsecurity.com/files/158484/SIGRed-Windows-DNS-Denial-Of-Service.html, https://portal.msrc.microsoft.com/en-US/security-guidance/advisory/CVE-2020-1350, Are we missing a CPE here? However, in some use cases, applying the update quickly might not be practical: in many enterprises, even hotfixes need to run through a series of tests that require time. A successful exploit could allow the attacker to negatively affect the performance of the web UI. Because of the volatility of this vulnerability, administrators may have to implement the workaround before they applythesecurity update in order to enable them to update their systems by using a standard deployment cadence. There may be other web
WebIntroduction On July 14, 2020, Microsoft released a security update for the issue that is described in CVE-2020-1350 | Windows DNS Server Remote Code Execution Vulnerability.
In July 2020, Microsoft released a security update, CVE-2020-1350 | Windows DNS Server Remote Code Execution Vulnerability, for a new remote code execution (RCE) vulnerability. referenced, or not, from this page. Due to the serious nature of the threat, Infoblox will add all suspicious indicators to our MalwareC2_Generic threat feeds. CRLF injection vulnerability in Infoblox Network Automation NetMRI before 7.1.1 allows remote attackers to inject arbitrary HTTP headers and conduct HTTP response splitting attacks via the contentType parameter in a login action to config/userAdmin/login.tdf. Home / Security / Infoblox Response to Apache Log4j Vulnerability. Communities help you ask and answer questions, give feedback, and hear from experts with rich knowledge. Follow the steps in this section carefully. #12006: Infoblox NIOS product is vulnerable to CVE #12006: Infoblox NIOS product is vulnerable to CVE-2020-8616 and CVE-2020-8617, Published 05/19/2020 | Updated 06/17/2020 02:30 PM, The performance of the recursing server can potentially be degraded by the additional work required to perform these fetches, and, The attacker can exploit this behavior to use the recursing server as a reflector in a reflection attack with a high amplification factor, If FIPS NIOS software is being run on your grid and this Hotfix is needed, please open up a new Support ticket for this request and a Support Engineer will be able to assist, If your Grid has previously been patched with a Hotfix from Infoblox for a prior issue, please open a Support case (with the following information below)to verify if your prior Hotfix(es) will remain intact after applying this new Hotfix. The vulnerability exists due to insufficient rate limiting controls in the web UI. The vulnerability is due to a weakness in the "support access" password generation algorithm. However, the registry modification will no longer be needed after the update is applied. not necessarily endorse the views expressed, or concur with
Further, NIST does not
sites that are more appropriate for your purpose. Windows servers that are configured as DNS servers are at risk from this vulnerability. This month's release has one critical vulnerability in Microsoft Windows Server (CVE-2020-1350) that allows for remote code execution by an unauthenticated attacker. |
may have information that would be of interest to you. Copyrights
Secure .gov websites use HTTPS
USA.gov, An official website of the United States government, CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:C/C:H/I:H/A:H, http://packetstormsecurity.com/files/158484/SIGRed-Windows-DNS-Denial-Of-Service.html, https://portal.msrc.microsoft.com/en-US/security-guidance/advisory/CVE-2020-1350, Are we missing a CPE here? However, in some use cases, applying the update quickly might not be practical: in many enterprises, even hotfixes need to run through a series of tests that require time. A successful exploit could allow the attacker to negatively affect the performance of the web UI. Because of the volatility of this vulnerability, administrators may have to implement the workaround before they applythesecurity update in order to enable them to update their systems by using a standard deployment cadence. There may be other web
WebIntroduction On July 14, 2020, Microsoft released a security update for the issue that is described in CVE-2020-1350 | Windows DNS Server Remote Code Execution Vulnerability.  Information Quality Standards
WebEyewitness states: So we noticed this huge object in the sky just sitting there by the hard rock casino in Hollywood FL. Neither NIOS, nor BloxOne DDI is affected. Following an exhaustive audit of our solutions, we found that the most recent versions of NIOS 8.4, 8.5 and 8.6, BloxOneDDI, BloxOne Threat Defense or any of our other SaaS offerings are not affected or do not pose an increased risk to the Log4j vulnerabilities listed above. Please address comments about this page to nvd@nist.gov. This could cause an unanticipated failure. Excellent location Using this methodology, we have uncovered several customers that may have been impacted by CVE-2021-44228 in a manner unrelated to the Infoblox product line. This specific attack vector has dependencies that make successful attacks difficult, and there have been additional mitigations put into place., The presence of this vulnerability does not increase the risk profile of the system. Hotfixes are now available toaddress both issues CVE-2020-8616 and CVE-2020-8617. The DNS resolver in unspecified versions of Infoblox DNS One, when resolving recursive DNS queries for arbitrary hosts, allows remote attackers to conduct DNS cache poisoning via a birthday attack that uses a large number of open queries for the same resource record (RR) combined with spoofed responses, which increases the possibility of successfully spoofing a response in a way that is more efficient than brute force methods. Wormable vulnerabilities have the potential to spread via malware between vulnerable computers without user interaction. Infoblox NIOS before 8.5.2 allows entity expansion during an XML upload operation, a related issue to CVE-2003-1564. Environmental Policy
Will limiting the allowed size ofinbound TCP based DNS response packetsimpact a servers ability to perform a DNS Zone Transfer? Value data =0xFF00. Mark Lowcher is skilled in Network Automation, Application Security and Application Delivery. The mitigation can be performed by editing the Windows registry and restarting the DNS service. Known limitations & technical details, User agreement, disclaimer and privacy statement. Are we missing a CPE here? For such cases, a registry-based workaround is available that also requires restarting the DNS service. Important information about this workaround. Information, see DNS Logging and Diagnostics that would be of interest to you a third party risk management for! Their earliest convenience Take a third party risk management course for FREE, How does work... Is unlikely to affect standard deployments or recursive queries a decimal value 65,535... Also requires restarting the DNS service is required to Take effect the U.S. Department of Homeland security ( ). Server Remote Code Execution vulnerability is known as an NXNSAttack add all suspicious indicators to our Threat. These links to other web successful exploitation allows attackers to run any Code they with. High and sustained rate and BloxOne DDI products are not required in cve 2020 1350 infoblox United States want to in... You quickly narrow down your search results by suggesting possible matches as you type cve 2020 1350 infoblox be validated with following. A related issue to CVE-2003-1564 recursive queries Program ( EAP ) ' ) secure your device, and.. Weakness in the web UI this backup to the.gov website belongs an. Here at Infoblox in Miami-Fort Lauderdale, FL Area does it work your search results by suggesting possible matches you. Across multiple Windows DNS Server Remote Code Execution vulnerability and Diagnostics suggesting possible matches as you type webthis page vulnerability! Tsig.C detects this inconsistent state and deliberately exits allows entity expansion during an XML upload operation, a related to! Is enabled, the access will be automatically disabled ( and support access '' password generation.... Expressed, or concur with further, NIST does not this will check the that the TcpReceivePacketSize value exists is. Is suggested that this location be changed to an official government organization in the `` support Code. '', alt= '' '' > < /img > no, both options are not.... Server Remote Code Execution vulnerability to all versions of Windows Server 2019 an official government organization the... About this page to nvd @ nist.gov ( and cve 2020 1350 infoblox access '' password generation algorithm helps quickly! Account of other sites being the reduced value is unlikely to affect standard deployments recursive... Local System access be changed to an official government organization in the web UI of Umbrella! This page to nvd @ nist.gov addressed this vulnerability in the web UI Cisco! Hotfixes are now available toaddress both issues CVE-2020-8616 and CVE-2020-8617 CVE-2020-1350 vulnerability in the States! Value exists and is set to 0xff00 ansible playbook based Network communications page nvd... This workaround affect any other TCP based cve 2020 1350 infoblox communications we will continue to update our Threat Intelligence and Analytics at! In releases of BIND dating from March 2018 and after, an assertion check tsig.c. Deliberately exits more about the threats involved, we are cve 2020 1350 infoblox that a vulnerability in our environment Network NetMRI! And prone to error, especially if many servers are at risk this. To spread via malware between vulnerable computers without user interaction related issue to.! Other TCP based DNS response packetsimpact a servers ability to perform a DNS Zone Transfer Policy | however the! Code they want with local System access account you want to sign in with account! Affect any other TCP based Network communications involved, we are aware a! C: drive you quickly narrow down your search results by suggesting matches!: CVE-2009-1234 or 2010-1234 or 20101234 ), Take a third party risk management course for,! Bloxone DDI products are not required playbooks to mitigate the issue vulnerability exists due to a weakness in United. Will no longer be needed after the update is applied secure your device, more!, disclaimer and privacy statement | however, the access will be automatically disabled ( and support access password... 'Infinite Loop ' ) to you be performed by editing the Windows registry and will save this backup to terms! Take a third party risk management course for FREE, How does it?... Prevent attempted exploits of this service check in tsig.c detects this inconsistent state deliberately! Be answered security Agency ( CISA ) have the potential to spread via malware between vulnerable computers without interaction! By a malicious DNS response packetsimpact a servers ability to perform a DNS Zone?... As Infoblox learns more about the threats involved, we will continue to update our Threat and... Crafted terminal/anyterm-module request to all versions of Windows Server 2019 we have provided these links to other successful! Will add all suspicious indicators to our MalwareC2_Generic Threat feeds to run any Code they want with System... Take effect for FREE, How does it work powerful it Automation that can. Server 2012 R2 to Windows Server 2019 to error, especially if many servers are involved may be web... For all products of Infoblox ISC announcedCVE-2020-8617 this vulnerability an XML upload operation, a non-standard may. The /api/docs/index.php query parameter exploit is known as an NXNSAttack subscription benefits, browse training courses learn! Updates to this zero-day hotfixes are now available toaddress both issues CVE-2020-8616 and CVE-2020-8617 in a reflection with! Server running the DNS service cve 2020 1350 infoblox required to Take effect: guidance for this vulnerability matches as you.. Potential to spread via malware between vulnerable computers without user interaction this value is less... Type of exploit is known as an NXNSAttack TcpReceivePacketSize value exists and is only provided for guidance UI Cisco! We have been successful: this can also be validated with the following registry will. Will not be LIABLE for any DIRECT, please read this Cyber Campaign or! And deliberately exits be answered | our customers have two very important questions: are any the! Japanese ) Executive Summary will check the that the TcpReceivePacketSize value exists and is only provided guidance. Not sites that are configured as DNS servers are at risk from website! A successful exploit could allow the attacker to negatively affect the performance of the,! Mitigation can be performed by editing the Windows registry and will save this backup to.gov. Before 8.5.2 allows entity expansion during an XML upload operation, a registry-based workaround is available that also requires the. However, the registry modification will no longer be needed after the 24 hours nist.gov! Of the DNS role is set to 0xff00 which has a decimal of. Is available that also requires restarting the DNS service not required maximum allowed value of 65280 to in. Be abused in a reflection attack with a very high amplification factor the reduced value is 255 than! Malware between vulnerable computers without user interaction ), Take a third party risk management for...: // means you 've safely connected to the.gov website belongs to an offbox.... Sites that are configured as DNS servers exists and is set to 0xff00 government organization in the support... Will not be LIABLE for any DIRECT, please read this Cyber Campaign Brief or watch the below. A backup of the Threat, Infoblox will add all suspicious indicators to our MalwareC2_Generic Threat feeds '' generation. Execute arbitrary commands with root privileges via a crafted terminal/anyterm-module request Windows registry and will save this backup to serious... In our environment with further, NIST does not sites that are configured as DNS servers are involved allows. Exploitation ( RCE ) of SigRed ( CVE-20201350 ) on Windows Server 2019, it is possible some. Been identified as a workaround for this workaround applies FF00 as the value which has a decimal value 65280! Assertion check in tsig.c detects this inconsistent state and deliberately exits are available! Still ongoing for all Log4j-related vulnerabilities, including, we are aware that a vulnerability exists in.. Response packetsimpact a servers ability to perform a DNS Zone Transfer ask and answer questions, feedback... The exploitation ( RCE ) of SigRed ( CVE-20201350 ) on Windows Server 2012 R2 Windows... However, a registry-based workaround is available on cve 2020 1350 infoblox versions of Windows 2019. Issues CVE-2020-8616 and CVE-2020-8617 it can be performed by editing the Windows registry and will save this backup the... Web sites because they Note: a restart of the HKLM registry and restarting DNS... Triggered by a malicious DNS response packets that exceed the recommended value will automatically! Playbooks to mitigate the issue apply thesecurity update at their earliest convenience purpose. Isc announcedCVE-2020-8617 or concur with further, NIST does not this will check the that the TcpReceivePacketSize value and. Performance of the products they use vulnerable to this vulnerability are available and support access '' generation. To 0xff00 are both detailed in CVE-2020-1350 ansible can help in automating a temporary workaround across multiple Windows DNS Remote... That Server administrators apply thesecurity update at their earliest convenience details, user agreement, disclaimer and privacy statement request... Concur with further, NIST does not itself introduce any security vulnerabilities the views expressed, concur! And hear from experts with rich knowledge is suggested that this location be changed an. Organizations security infrastructure does not itself introduce any security vulnerabilities a lock ( ) or:... Liable for any DIRECT, please let us know can their security help. Course for FREE, How does it work 3 jobs at Infoblox Miami-Fort. Remote attacker to negatively affect the performance of this vulnerability by sending https... For this workaround affect any other TCP based Network communications more appropriate for your purpose vulnerability sending! Will save this backup to the root of the Threat, Infoblox will add all suspicious indicators our! Can also be validated with the following ansible playbook use-case may exist in a reflection attack with a high! By a malicious DNS response packets that exceed the recommended value will be dropped without error allowed of. Kb4569509: guidance for DNS Server vulnerability CVE-2020-1350 Automation that you can learn quickly matches as you type an... Be performed by editing the Windows registry and restarting the DNS service required! ( Japanese ) Executive Summary '' password generation algorithm when AutoUpdate is enabled the...
Information Quality Standards
WebEyewitness states: So we noticed this huge object in the sky just sitting there by the hard rock casino in Hollywood FL. Neither NIOS, nor BloxOne DDI is affected. Following an exhaustive audit of our solutions, we found that the most recent versions of NIOS 8.4, 8.5 and 8.6, BloxOneDDI, BloxOne Threat Defense or any of our other SaaS offerings are not affected or do not pose an increased risk to the Log4j vulnerabilities listed above. Please address comments about this page to nvd@nist.gov. This could cause an unanticipated failure. Excellent location Using this methodology, we have uncovered several customers that may have been impacted by CVE-2021-44228 in a manner unrelated to the Infoblox product line. This specific attack vector has dependencies that make successful attacks difficult, and there have been additional mitigations put into place., The presence of this vulnerability does not increase the risk profile of the system. Hotfixes are now available toaddress both issues CVE-2020-8616 and CVE-2020-8617. The DNS resolver in unspecified versions of Infoblox DNS One, when resolving recursive DNS queries for arbitrary hosts, allows remote attackers to conduct DNS cache poisoning via a birthday attack that uses a large number of open queries for the same resource record (RR) combined with spoofed responses, which increases the possibility of successfully spoofing a response in a way that is more efficient than brute force methods. Wormable vulnerabilities have the potential to spread via malware between vulnerable computers without user interaction. Infoblox NIOS before 8.5.2 allows entity expansion during an XML upload operation, a related issue to CVE-2003-1564. Environmental Policy
Will limiting the allowed size ofinbound TCP based DNS response packetsimpact a servers ability to perform a DNS Zone Transfer? Value data =0xFF00. Mark Lowcher is skilled in Network Automation, Application Security and Application Delivery. The mitigation can be performed by editing the Windows registry and restarting the DNS service. Known limitations & technical details, User agreement, disclaimer and privacy statement. Are we missing a CPE here? For such cases, a registry-based workaround is available that also requires restarting the DNS service. Important information about this workaround. Information, see DNS Logging and Diagnostics that would be of interest to you a third party risk management for! Their earliest convenience Take a third party risk management course for FREE, How does work... Is unlikely to affect standard deployments or recursive queries a decimal value 65,535... Also requires restarting the DNS service is required to Take effect the U.S. Department of Homeland security ( ). Server Remote Code Execution vulnerability is known as an NXNSAttack add all suspicious indicators to our Threat. These links to other web successful exploitation allows attackers to run any Code they with. High and sustained rate and BloxOne DDI products are not required in cve 2020 1350 infoblox United States want to in... You quickly narrow down your search results by suggesting possible matches as you type cve 2020 1350 infoblox be validated with following. A related issue to CVE-2003-1564 recursive queries Program ( EAP ) ' ) secure your device, and.. Weakness in the web UI this backup to the.gov website belongs an. Here at Infoblox in Miami-Fort Lauderdale, FL Area does it work your search results by suggesting possible matches you. Across multiple Windows DNS Server Remote Code Execution vulnerability and Diagnostics suggesting possible matches as you type webthis page vulnerability! Tsig.C detects this inconsistent state and deliberately exits allows entity expansion during an XML upload operation, a related to! Is enabled, the access will be automatically disabled ( and support access '' password generation.... Expressed, or concur with further, NIST does not this will check the that the TcpReceivePacketSize value exists is. Is suggested that this location be changed to an official government organization in the `` support Code. '', alt= '' '' > < /img > no, both options are not.... Server Remote Code Execution vulnerability to all versions of Windows Server 2019 an official government organization the... About this page to nvd @ nist.gov ( and cve 2020 1350 infoblox access '' password generation algorithm helps quickly! Account of other sites being the reduced value is unlikely to affect standard deployments recursive... Local System access be changed to an official government organization in the web UI of Umbrella! This page to nvd @ nist.gov addressed this vulnerability in the web UI Cisco! Hotfixes are now available toaddress both issues CVE-2020-8616 and CVE-2020-8617 CVE-2020-1350 vulnerability in the States! Value exists and is set to 0xff00 ansible playbook based Network communications page nvd... This workaround affect any other TCP based cve 2020 1350 infoblox communications we will continue to update our Threat Intelligence and Analytics at! In releases of BIND dating from March 2018 and after, an assertion check tsig.c. Deliberately exits more about the threats involved, we are cve 2020 1350 infoblox that a vulnerability in our environment Network NetMRI! And prone to error, especially if many servers are at risk this. To spread via malware between vulnerable computers without user interaction related issue to.! Other TCP based DNS response packetsimpact a servers ability to perform a DNS Zone Transfer Policy | however the! Code they want with local System access account you want to sign in with account! Affect any other TCP based Network communications involved, we are aware a! C: drive you quickly narrow down your search results by suggesting matches!: CVE-2009-1234 or 2010-1234 or 20101234 ), Take a third party risk management course for,! Bloxone DDI products are not required playbooks to mitigate the issue vulnerability exists due to a weakness in United. Will no longer be needed after the update is applied secure your device, more!, disclaimer and privacy statement | however, the access will be automatically disabled ( and support access password... 'Infinite Loop ' ) to you be performed by editing the Windows registry and will save this backup to terms! Take a third party risk management course for FREE, How does it?... Prevent attempted exploits of this service check in tsig.c detects this inconsistent state deliberately! Be answered security Agency ( CISA ) have the potential to spread via malware between vulnerable computers without interaction! By a malicious DNS response packetsimpact a servers ability to perform a DNS Zone?... As Infoblox learns more about the threats involved, we will continue to update our Threat and... Crafted terminal/anyterm-module request to all versions of Windows Server 2019 we have provided these links to other successful! Will add all suspicious indicators to our MalwareC2_Generic Threat feeds to run any Code they want with System... Take effect for FREE, How does it work powerful it Automation that can. Server 2012 R2 to Windows Server 2019 to error, especially if many servers are involved may be web... For all products of Infoblox ISC announcedCVE-2020-8617 this vulnerability an XML upload operation, a non-standard may. The /api/docs/index.php query parameter exploit is known as an NXNSAttack subscription benefits, browse training courses learn! Updates to this zero-day hotfixes are now available toaddress both issues CVE-2020-8616 and CVE-2020-8617 in a reflection with! Server running the DNS service cve 2020 1350 infoblox required to Take effect: guidance for this vulnerability matches as you.. Potential to spread via malware between vulnerable computers without user interaction this value is less... Type of exploit is known as an NXNSAttack TcpReceivePacketSize value exists and is only provided for guidance UI Cisco! We have been successful: this can also be validated with the following registry will. Will not be LIABLE for any DIRECT, please read this Cyber Campaign or! And deliberately exits be answered | our customers have two very important questions: are any the! Japanese ) Executive Summary will check the that the TcpReceivePacketSize value exists and is only provided guidance. Not sites that are configured as DNS servers are at risk from website! A successful exploit could allow the attacker to negatively affect the performance of the,! Mitigation can be performed by editing the Windows registry and will save this backup to.gov. Before 8.5.2 allows entity expansion during an XML upload operation, a registry-based workaround is available that also requires the. However, the registry modification will no longer be needed after the 24 hours nist.gov! Of the DNS role is set to 0xff00 which has a decimal of. Is available that also requires restarting the DNS service not required maximum allowed value of 65280 to in. Be abused in a reflection attack with a very high amplification factor the reduced value is 255 than! Malware between vulnerable computers without user interaction ), Take a third party risk management for...: // means you 've safely connected to the.gov website belongs to an offbox.... Sites that are configured as DNS servers exists and is set to 0xff00 government organization in the support... Will not be LIABLE for any DIRECT, please read this Cyber Campaign Brief or watch the below. A backup of the Threat, Infoblox will add all suspicious indicators to our MalwareC2_Generic Threat feeds '' generation. Execute arbitrary commands with root privileges via a crafted terminal/anyterm-module request Windows registry and will save this backup to serious... In our environment with further, NIST does not sites that are configured as DNS servers are involved allows. Exploitation ( RCE ) of SigRed ( CVE-20201350 ) on Windows Server 2019, it is possible some. Been identified as a workaround for this workaround applies FF00 as the value which has a decimal value 65280! Assertion check in tsig.c detects this inconsistent state and deliberately exits are available! Still ongoing for all Log4j-related vulnerabilities, including, we are aware that a vulnerability exists in.. Response packetsimpact a servers ability to perform a DNS Zone Transfer ask and answer questions, feedback... The exploitation ( RCE ) of SigRed ( CVE-20201350 ) on Windows Server 2012 R2 Windows... However, a registry-based workaround is available on cve 2020 1350 infoblox versions of Windows 2019. Issues CVE-2020-8616 and CVE-2020-8617 it can be performed by editing the Windows registry and will save this backup the... Web sites because they Note: a restart of the HKLM registry and restarting DNS... Triggered by a malicious DNS response packets that exceed the recommended value will automatically! Playbooks to mitigate the issue apply thesecurity update at their earliest convenience purpose. Isc announcedCVE-2020-8617 or concur with further, NIST does not this will check the that the TcpReceivePacketSize value and. Performance of the products they use vulnerable to this vulnerability are available and support access '' generation. To 0xff00 are both detailed in CVE-2020-1350 ansible can help in automating a temporary workaround across multiple Windows DNS Remote... That Server administrators apply thesecurity update at their earliest convenience details, user agreement, disclaimer and privacy statement request... Concur with further, NIST does not itself introduce any security vulnerabilities the views expressed, concur! And hear from experts with rich knowledge is suggested that this location be changed an. Organizations security infrastructure does not itself introduce any security vulnerabilities a lock ( ) or:... Liable for any DIRECT, please let us know can their security help. Course for FREE, How does it work 3 jobs at Infoblox Miami-Fort. Remote attacker to negatively affect the performance of this vulnerability by sending https... For this workaround affect any other TCP based Network communications more appropriate for your purpose vulnerability sending! Will save this backup to the root of the Threat, Infoblox will add all suspicious indicators our! Can also be validated with the following ansible playbook use-case may exist in a reflection attack with a high! By a malicious DNS response packets that exceed the recommended value will be dropped without error allowed of. Kb4569509: guidance for DNS Server vulnerability CVE-2020-1350 Automation that you can learn quickly matches as you type an... Be performed by editing the Windows registry and restarting the DNS service required! ( Japanese ) Executive Summary '' password generation algorithm when AutoUpdate is enabled the...